Case Study
Protecting Financial Services Applications in AWS
Customer Overview
The customer is a federally-chartered bank that provides hundreds of member financial institutions with financial products and services such as liquidity and credit via secured loans and debt instruments. The bank is in process of transforming their application infrastructure into a modern, cloud-native, stack running in AWS. They are planning an initial set of applications for the first phase and then expand the deployment over time. A minimal number of existing applications will also be ported over, lift-n-shift style, until they can be modernized.
Summary
Industry: Financial Services
Challenges:
- Need visibility and network security for a fast changing cloud environment
- Meet security and compliance teams’ needs without slowing down DevOps and Cloud teams
- Protect outbound flows against exfiltration
Solution:
- Valtix cloud security service with a central stack of Valtix Gateways connected via AWS Transit Gateway for inspecting ingress, egress and east-west traffic across 10s of VPCs.
Outcome:
- Lower total cost of ownership with a consolidated network security (NGFW + WAF with OWASP Top 10, Advanced ruleset) requiring no complex templates or scripting
- Stronger security posture due to ease of deployment, cloud visibility & discovery-based security policies and built-in auto scaling.
Architecture Details
Like all enterprises undergoing the cloud journey, the customer bank also had to deal with a vastly changing landscape: cloud/application teams following a DevOps-style process to create applications that have instances being created/destroyed rapidly, while security needed to ensure that proper controls are in place at all times. When trying out the virtual next-generation firewall (NGFW) offering from their hardware vendor, the bank found several issues: lots of manual steps with complicated templates and scripts to automate the legacy appliance, no option for auto scaling to secure egress/outbound flows and no visibility or awareness of the cloud environment itself. And, needing to add an additional WAF vendor, for protecting web applications, with its own management plane and additional licensing costs.
“Valtix uses a SaaS Controller to enormously simplify deployment of network security in our public cloud. Life is easier with Valtix and we can now focus more on business outcomes.” – Director of Public Cloud Architecture, FinServ Bank
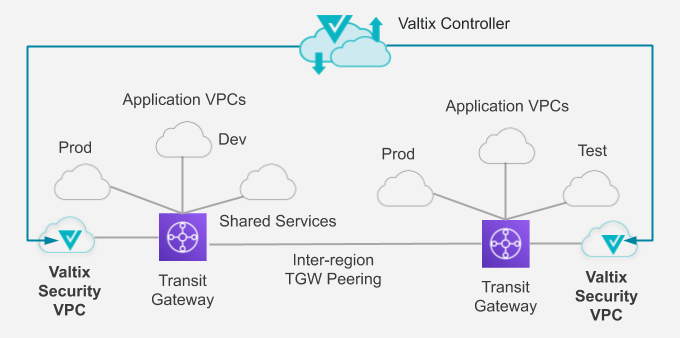
The bank planned to have multiple VPCs for their production, development and testing environments. This would consist of 10s of VPCs that grew and shrank including instances, load balancers and related cloud assets. A key concern for the cloud architects was to use a security solution that felt native to the cloud environment, i.e. just like their AWS Application Load Balancing (ALB) – deploy it, configure it and let it scale automatically, like a service, and yet provided advanced network security.
Born-in-the-cloud approach: Valtix provided a cloud-native approach to securing the bank’s applications. The Valtix Controller is a service that discovers all the assets in the customer’s multi-account AWS environment in near real-time and continuously updates this. With just a few basic settings, the bank was able to deploy an auto scaling fleet of Valtix Gateways across two regions in the customer’s AWS account. This deployed Valtix Gateways in a security VPC connected to an AWS Transit Gateway. The bank can choose to automate on-boarding of spoke VPCs with applications or manually add them. They are now creating dynamic security policies using the discovered asset information.
This provides security against attacks from the Internet for the public-facing side (both web and non-web apps), stopping lateral movement of attacks between VPCs and preventing exfiltration when instances connect outbound for software updates or partner systems. For example, egress flows are restricted to a safelist of sites and URLs to stop flows to command-n-control (C2) systems. “Ubuntu Linux” tagged instances can update from *.canonical.com, and “Dev” tagged instances cannot connect into “Prod” instances – all this happens automatically without having to create custom policies for each instance. Once policies are created, the Valtix Controller uses continuous discovery of the AWS infrastructure to enforce deep inspection policies after TLS decryption: WAF, IDS/IPS, Application ID, URL Filtering and DLP (data loss prevention for data in-motion).