Valtix Brings Flexibility in Cloud Network Security Architecture
Another quarter, another update to the Valtix cloud security service. As always, the Valtix Controller (management plane) is updated automatically just like a SaaS, and the Valtix Gateways (dataplane) running in your cloud account can be updated with one-click (blue/green with hitless updates and zero downtime). Here’s what’s new in the June 2021 update (labelled version 2.8):
- Combined East-West & Egress Gateways
- Timeseries Log Analytics
- Diff’s on Policy Changes
- Admin User Management Improvements
- Changes in Valtix Gateway Deployment
- Bug fixes
All of these features are driven by customer feedback and continue to build on the visibility features we introduced in March (version 2.7). To learn more see docs.valtix.com/userguide
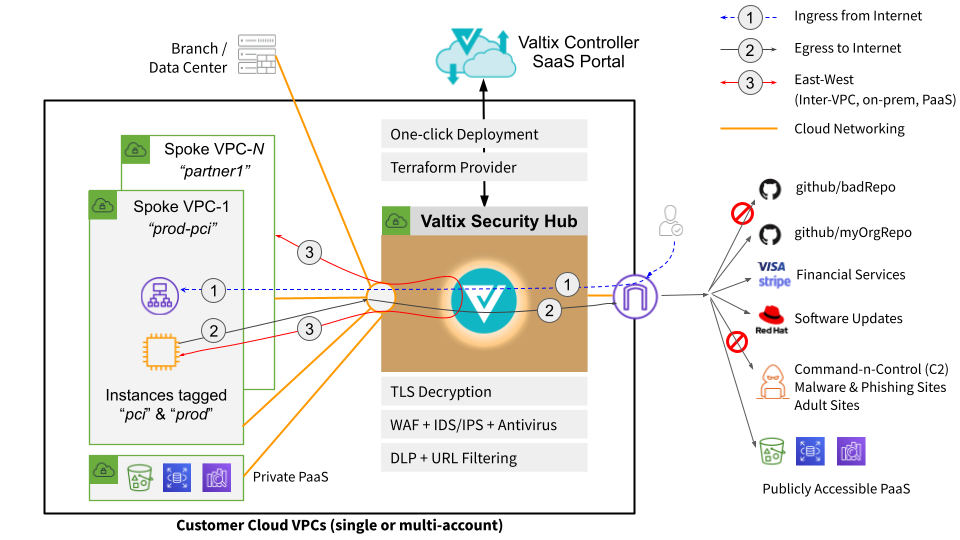
Combined East-West & Egress Gateways
Today, customers deploy a Valtix Gateway for each specific use case. Usually, the most common way to deploy this is to connect multiple application VPCs (spokes) to a central security VPC (hub). (Another option is to deploy a Valtix Gateway in each VPC/VNET and make a “secure island” of each VPC). So the security hub (services VPC in Valtix lingo) has a Valtix Gateway for:
- Ingress – protect Internet-facing applications (both web and non-web apps)
- Egress – stop exfiltration on outbound flows from your cloud deployment to the Internet
- East-West – block lateral movement of threats between VPCs, to PaaS, between clouds, and to on-premises networks
Now, Valtix cloud network security architecture gives you the flexibility to deploy with separate east-west and egress Gateways, or create a combined east-west and egress Gateway. The combined Gateway allows you to consolidate network security across multiple use cases. Separate Gateways for each use case allow a clearer segmentation to match the policy and business needs. For example, perimeter security (ingress and egress) is managed by a different team, while the east-west is a separate policy and management domain. If you choose to use the combined Gateway, make sure to increase the min/max auto-scaling settings to ensure there is sufficient elasticity in dealing with the increased traffic that must be inspected. For more information or guidance on which one to select, talk to your Sales Engineer or contact us at info@valtix.com
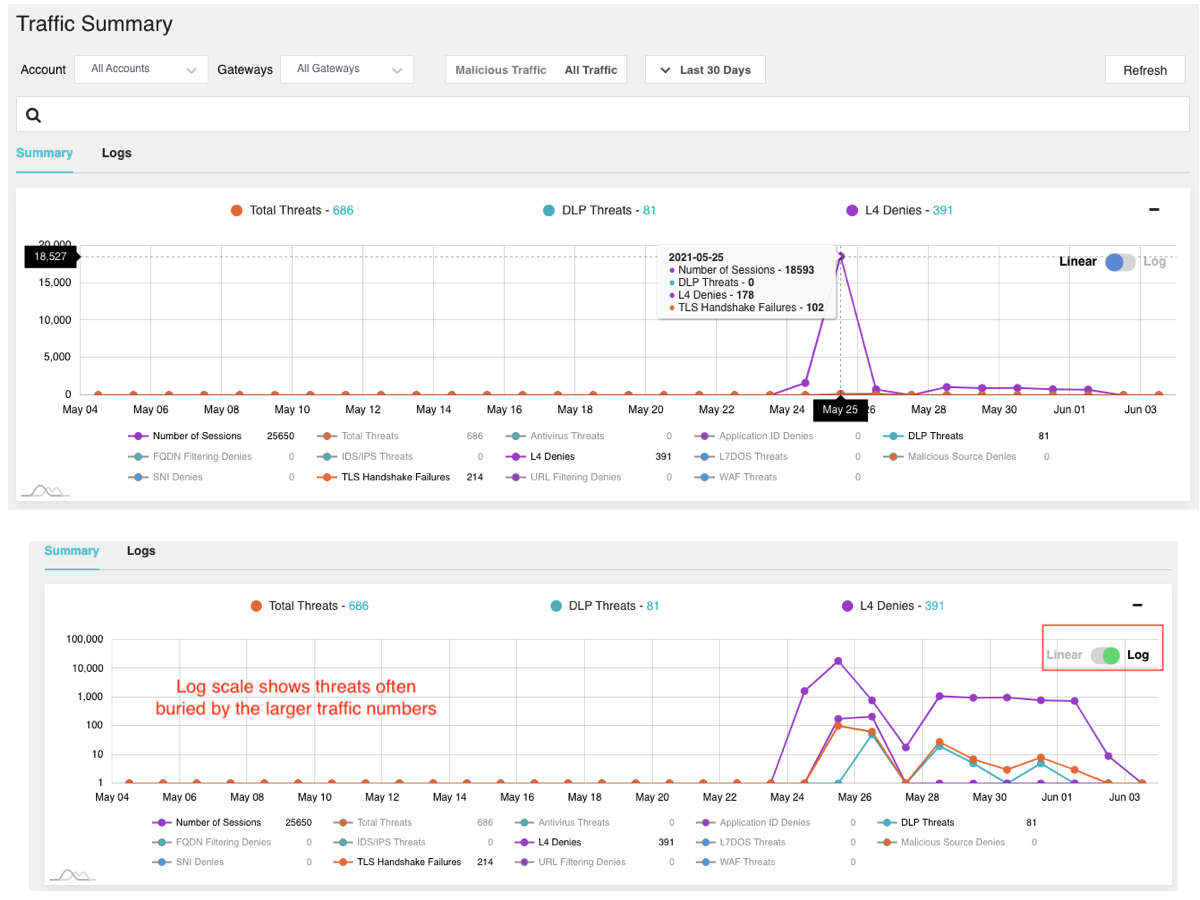
Time Series Log Analytics
As our customer base grows, security teams are looking for easier ways to understand the traffic and threat logs from Valtix Gateways. Now it’s easy to see all the data in one single view and with a few clicks analyze it across several dimensions:
- All traffic vs. malicious traffic
- Linear scale vs. log scale (find those small indicators of compromise quickly)
- Turn on/off specific metrics by clicking on the legend
- Mouseover on data points to see greater detail
- Top-level view across all cloud accounts (true multi-cloud visibility) or specific cloud accounts
- Pivot from charts to detailed logs with one-click (click Logs next to Summary)
- Select a particular time/area on the chart to drill down into the time window
- Minimize the time series chart (- button on right-top) to get a full page view of logs
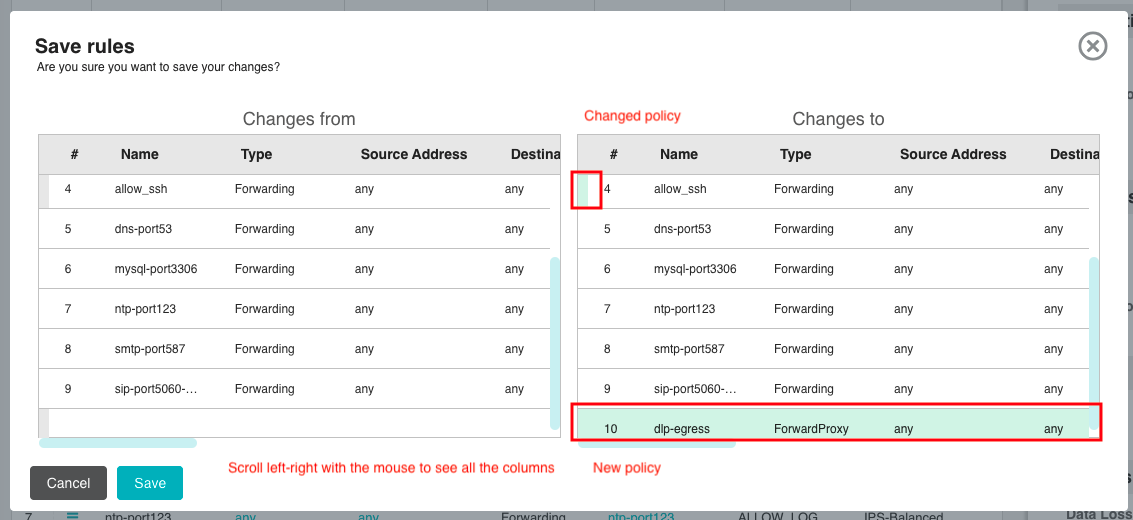
Diff’s on Policy Changes
As you start to build policies and make changes, you can now do a quick comparison before you save the changes to a number of policies within a ruleset. And you can scroll left-right to compare all the details, with synchronized scrolling to compare the relevant columns. New policies are shown with green background highlighting and changed policies have a little green bar on the left.
Admin User Management Improvements
Valtix administrators using the Valtix SaaS portal will notice a few changes:
- New login splash screen
- Reset password is directly built into the login screen so you don’t have to ask another person’s help to reset it for you. A reset password link is sent to the user’s registered email.
Changes in Valtix Gateway Deployment
There are a number of small detailed changes in Gateway deployment steps:
- Disabled Gateway-level SNAT by default – you can now instead enable a Service-level SNAT (Manage > Security Policies > Services) for forwarding mode traffic. Gateway-level SNAT is too broad for applying to an entire Gateway’s traffic flows.
- Removed unused instance types – as the public cloud evolves we’re doing the same. Less used instance types m4.2xlarge, c4.2xlarge are removed in favor of m5.2xlarge. This is only applicable to the SaaS portal GUI, Terraform can still use the older families.
- EBS Encryption – Valtix Gateway disks can now be encrypted with AWS-managed CMK or Customer managed encryption key.
- Added cloud region names – in addition to the region codes (af-south-1) you can see the geographic name: Africa (Cape Town).
- Show # of running Gateway instances – you can more prominently see the current number of running Gateway instances (3rd column in Manage > Gateways) instead of having to dive deep into Gateway details.
To try out Valtix or these new cloud network security architecture features in your cloud accounts, you can sign up at https://www.valtix.com/trial/ for a free 30-day trial. You can also get a free Cloud Visibility Report (CVR) to learn about the exposure of your cloud deployment to exfiltration attempts and command-n-control (C2) connections.