Valtix releases Google Cloud support with DevOps integration
Summary
Valtix continues to follow the cloud-native pattern of building features with a fast and agile CI/CD (continuous integration/continuous development) approach. This is something traditional next-generation firewall (NGFW) and web application firewall (WAF) appliance vendors cannot do with their once a year waterfall-style release cycles.
This builds on the June 2020 release that added protections against exfiltration using URL Filtering for egress/outbound traffic, usage metering, and Application ID. For details on each of these features, see the built-in documentation in your Valtix Controller portal.
Here’s a quick summary of the August 2020 (Valtix Gateway version 2.4) release:
- Google Cloud Platform (GCP) support – secure ingress, egress and east-west traffic to protect against attacks, exfiltration and lateral movement of attacks. Use the same consistent policies across your multi-cloud deployments.
- Terraform resource provider for Valtix – bake security right into the DevOps process. An auto scaling fleet of Valtix Gateways are ready for securing traffic within 3 minutes of deployment.
- Traffic Visibility Dashboard and Session Logs – top-level overview of traffic, including PaaS, by application types and source/destination IP addresses and countries.
- Data Loss Prevention (DLP) – allows specifying 30+ common data patterns such as credit card numbers, social security numbers (SSN), SSH keys, AWS secret keys, and PCRE (Perl Compatible Regular Expressions) data patterns.
- Threat Research – allows searching for specific CVEs or malware in your existing security policies to ensure coverage against the latest attacks, and searching through the Valtix database for web protection (Cloud WAF) and network intrusion (IDS/IPS) rules.
- Improvements to AWS Transit Gateway (TGW) workflow – makes it easier to use Valtix Gateways for cross-account usage to secure 10s-100s of VPCs.
- DataDog Integration – Logs can now be sent to your DataDog account in addition to the existing syslog and Splunk integrations.
How do I use/deploy these features?
In true cloud-native style, the Valtix Controller (aka management plane) has all the latest features upgraded automatically. And, the Valtix Gateways (aka dataplane) that are running in customer cloud accounts can be upgraded, i.e. fully under customer control, with a one-click blue/green hitless upgrade. Here are the steps:
- Go to Valtix Controller > Manage > Gateways
- Click on the ‘hamburger’ icon for your Gateway and select Upgrade
- Select the desired version for your Valtix Gateway
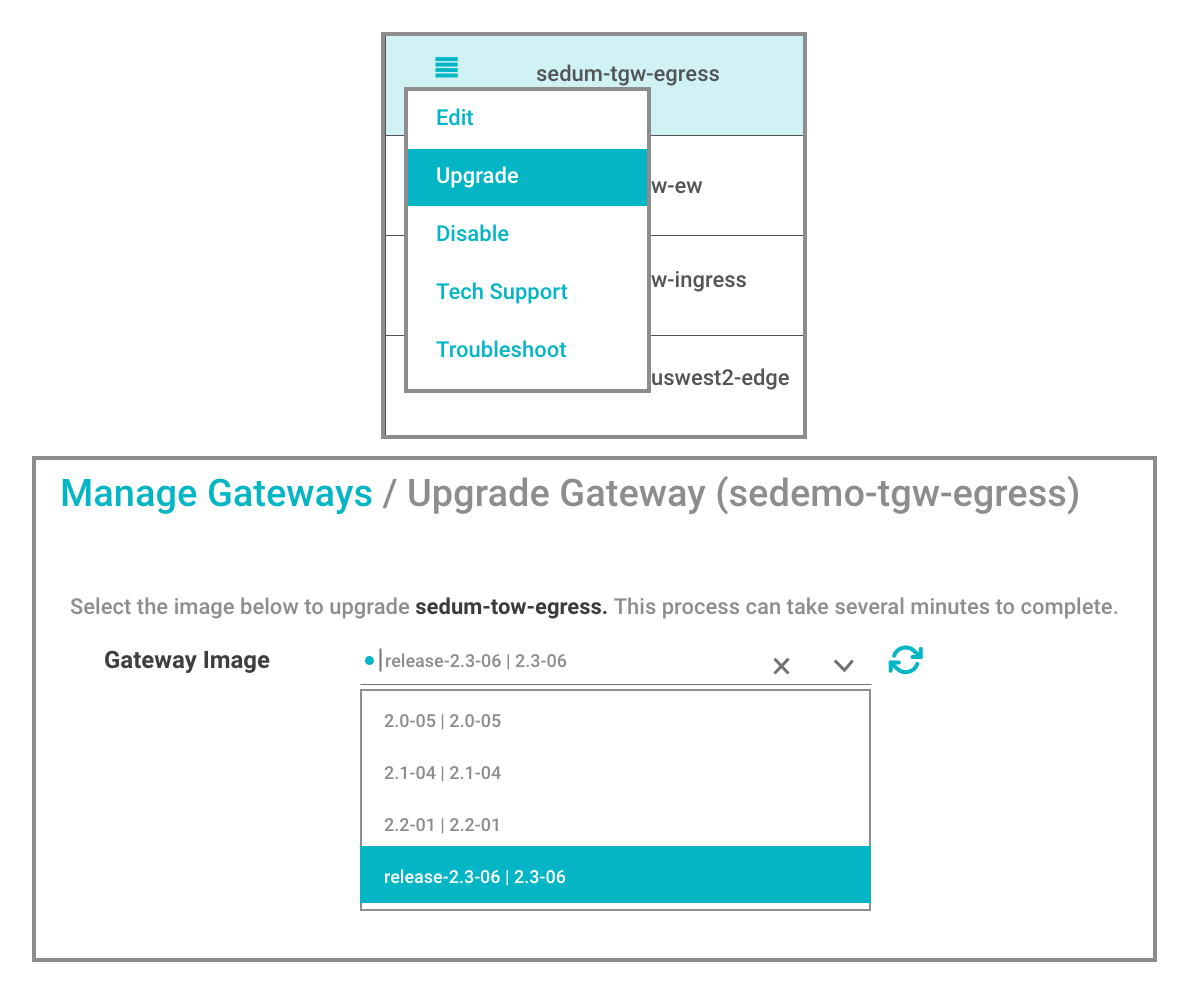
Valtix Controller will deploy a new fleet of Valtix Gateway instances (based on your per-AZ min / max auto scaling settings). The Controller will mark the old Gateways for termination and notify the frontend load balancer to start session draining. This will send all new traffic sessions to the new fleet, and continue existing sessions on the old Gateways. Once the old sessions terminate, the old Gateways will be automatically terminated.
This cloud-native blue/green upgrade process means that security administrators can focus on security and not spend multiple hours/days in tedious management tasks of upgrading software of traditional firewall appliances.
Google Cloud Platform (GCP) Support
Valtix now provides complete network security for your GCP deployments:
- Ingress – protect Internet-facing applications against attacks, both web and non-web/HTTP applications. You can build multi-layered security policies with the single-pass inspection after TLS decryption followed by WAF, IDS/IPS, and then re-encryption before sending it to the application backend which could be running on VMs/instances or containers managed by Kubernetes or GKE.
- Egress – protect outbound traffic from your cloud workloads against exfiltration by layering TLS decryption with URL filtering and FQDN access policies, IDS/IPS inspection and TLS re-encryption.
- East-West – protect against lateral movement of attacks between VPCs.
- PaaS – restrict access to compliance-related data buckets like PCI, PII, PHI data that ensures that a malicious insider or attacker on an instance with legitimate access cannot copy the data to personal or unauthorized destinations.
All of the security policies can be built with traditional IP and CIDR or modern attribute (aka tag) based security policies. For example:
- Egress Production Policies – Only allow “prod”, “Ubuntu” instances to connect to github.com/myOrgRepo and *.canonical.com. This makes sure that production systems can only connect to the org’s repo for infrastructure-as-code (IaC) usage and software updates from canonical.com.
- Egress Dev Policies – Allow “dev”, “Linux” instances to connect to anywhere on GitHub with access to github.com/* giving developers more flexibility during development.
- East-West Policies – Apply deep inspection policies for “partner” VPC connecting into a shared VPC’s “frontend”. This ensures that there is attribute-based access control (ABAC) and IDS/IPS inspection to stop lateral movement of attacks.
Terraform Resource Provider for Valtix – Bake Security Right into DevOps
Valtix now provides a Terraform resource provider for all the features of Valtix: Discover cloud assets by on-boarding your cloud assets, Deploy Valtix Gateways, and Defend with security policies. This allows deploying an auto-scaled fleet of Valtix Gateway instances ready to inspect traffic within 3 minutes of deployment. Security can now be also included as part of your continuous integration/continuous deployment (CI/CD) process. Customers can now directly bake security into their DevOps process – as applications are being deployed, security is built directly into the flow.
The Terraform resource provider of Valtix uses the REST API to make all the changes against the Valtix Controller for the automation. This can be used with all supported cloud providers: AWS, Azure, and GCP. To see detailed documentation, check the built-in documentation in your Valtix Controller portal. Documentation provides example variables.tf which will:
- Add GCP cloud project to the Valtix Controller
- Add an address object that represents a backend application that will be protected (proxied) by Valtix Gateway
- Add a service object to proxy the above address object by the Valtix Gateway
- Add a ruleset and a rule to allow traffic to the application from all sources on the internet
- Add a Valtix Gateway and assign the rule set to this Gateway.
For example, to onboard a GCP account running your applications to be protected with Valtix takes a few lines:
resource “valtix_cloud_account” gcp1 {
name = “gcpaccount”
csp_type = “GCP”
gcp_credentials_file = file(“valtix_controller_key.json”)
}
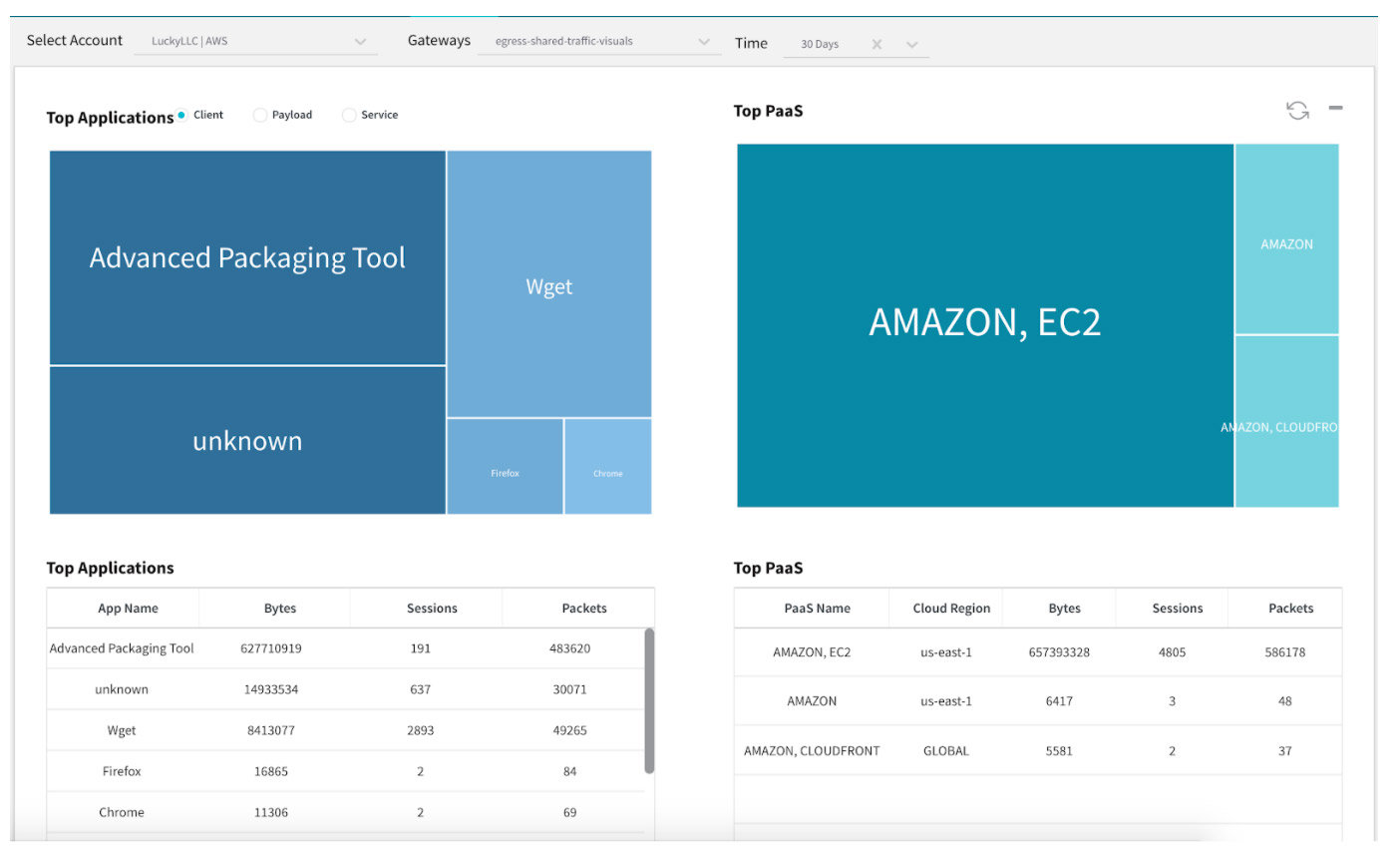
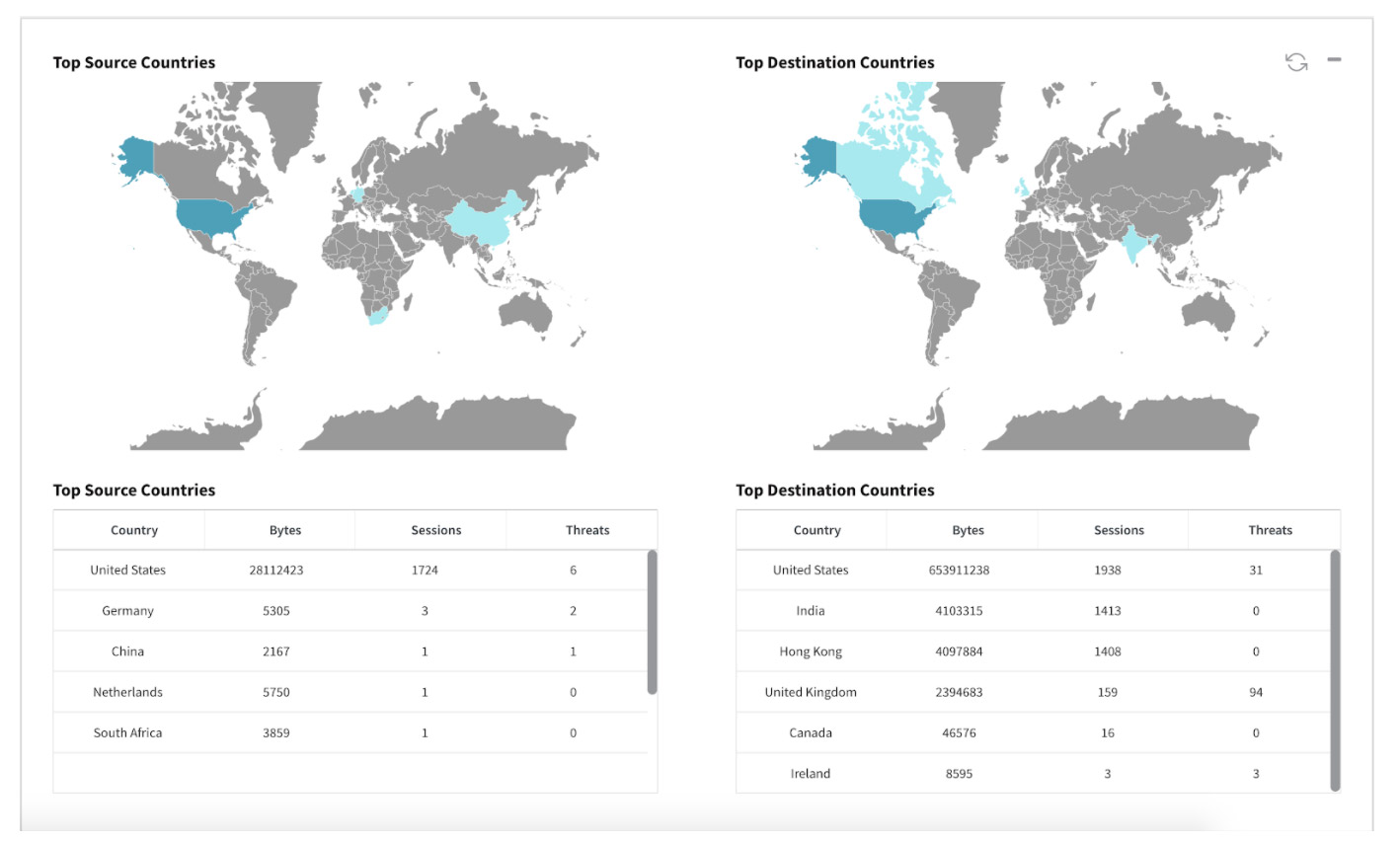
Traffic Visibility Dashboard & Session Logs
Valtix now features a top-level traffic visibility dashboard that shows aggregated information:
- Top Applications by client, payload inspection, or destination service
- PaaS for AWS and Azure
- Top Source and Destination Address Groups
- Top Source and Destination IP Addresses
- Top Source and Destination Countries
To see this dashboard go to your Valtix portal > Investigate > Traffic. Also, the Investigate > Logs section now features detailed Session logs to summarize all relevant information.
Data Loss Prevention (DLP) – Protect data-in-motion
DLP is especially useful for outbound/egress and PaaS (say AWS S3 buckets) traffic to ensure that data is not stolen as it is transiting the network. Valtix now includes protections against data loss prevention by specifying common data patterns such as credit card numbers, social security numbers (SSN), SSH keys, AWS secret keys, and PCRE (Perl Compatible Regular Expressions).
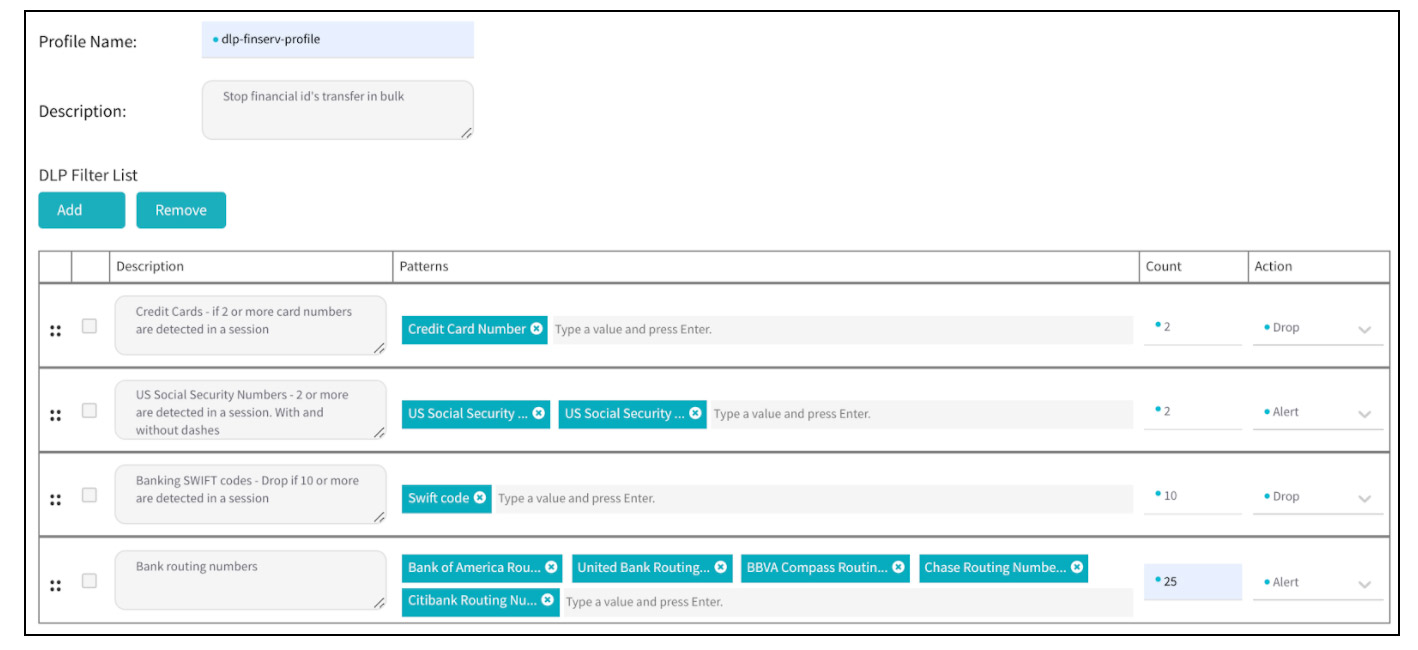
For example:
- Alert/Drop connections with SSH keys on outbound flows to GitHub – this prevents accidental sync of DevOps keys into your public GitHub repository.
- Alert for AWS secret and access keys
- A PCI application for processing credit cards may normally allow 2 credit cards to be used in processing a transaction. A DLP policy will ensure that if more than 2 credit cards are seen in a session, then Valtix will alert to DLP violation, i.e. if data loss is occurring where an attacker or malicious insider is exfiltrating multiple credit card numbers.
- Similarly, healthcare applications can use personal identifiers (SSN, Drivers license, credit card numbers), HIPAA PHI National Drug Codes and custom regular expressions. This can help organizations comply with HIPAA regulations to protect customer privacy.
- The DLP functionality can also be combined with Valtix discovered attributes of your instances to create intelligent security policies. So the DLP policies for Dev/Test environments can be lightweight (or focused only on credentials), while production systems can have higher-level of enforcement (like financial identifiers). So a policy would be that instances with tags of “prod” and “Linux” are inspected for the common data patterns to prevent exfiltration, while “dev” and “Linux” tagged systems are not inspected.
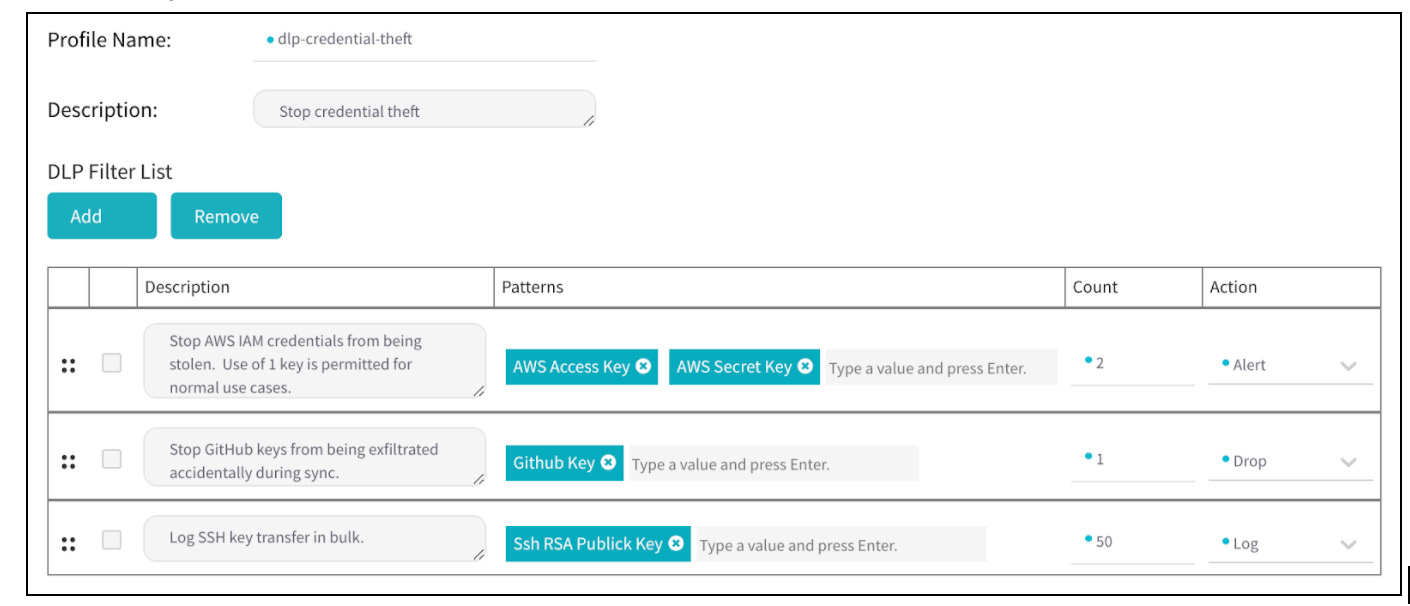
DLP policies can be attached to any Forward Proxy deployment of Valtix Gateways. To use DLP policies, from the Valtix Controller portal:
- Go to Manage > Network Intrusion > (right-top side) “Create Intrusion Profile” > Data Loss Prevention.
- Select either pre-defined patterns or create your PCRE (Perl-compatible regular expression) data patterns.
Threat Research – Quickly determine your security coverage
A frequent problem for security administrators is to know if they’re covered/protected against a new vulnerability or an old one. Now you can quickly search your existing/configured security rules to find out if the relevant CVE is already included in your web protection or network intrusion profiles. You can also search the Threat Research database to see which rules or profiles need to be added, in case you have not added them.
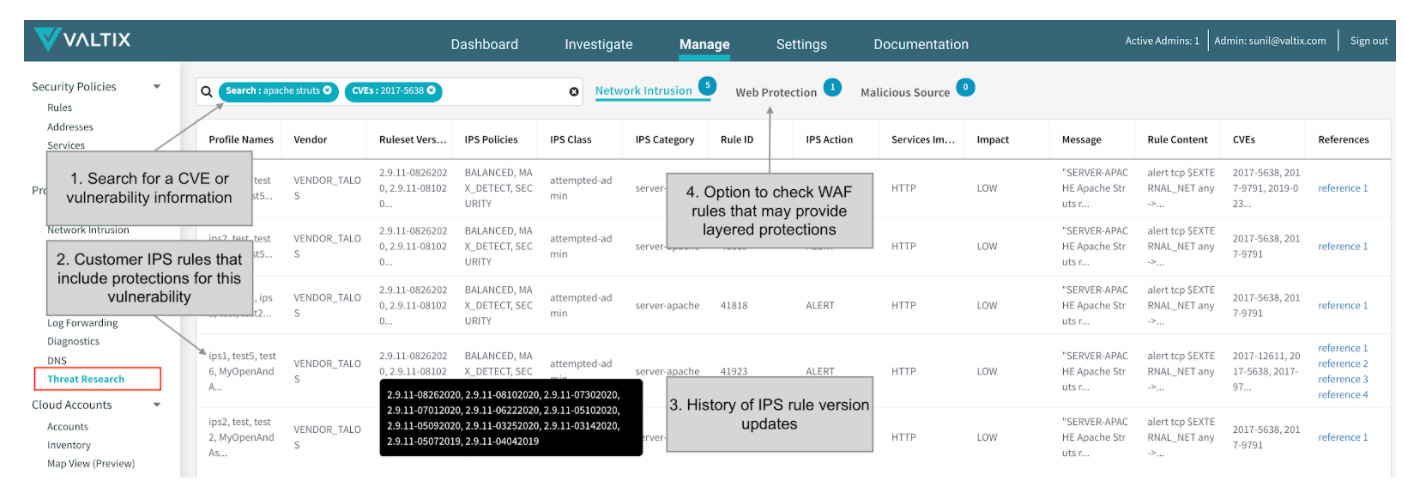
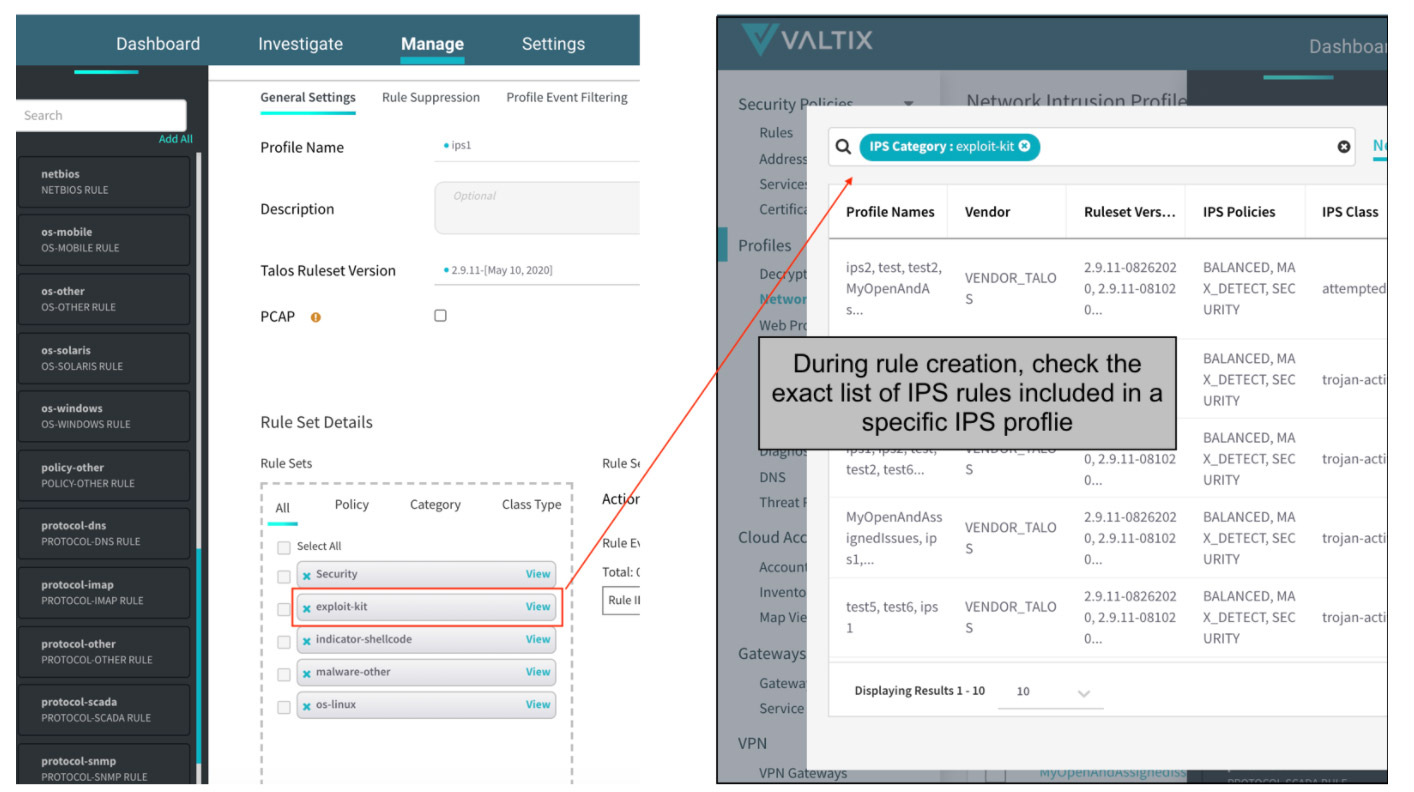
Improvements to AWS Transit Gateway (TGW)
AWS TGW setup can now use cross-account IAM roles to attach VPC’s from multiple AWS accounts. This adds to the existing ability to deploy TGW and connect across 10s and 100s of VPCs, and make necessary routing changes in the TGW to secure them via a security VPC running Valtix Gateways. Combined with Terraform support, customers can now easily secure these VPCs with automation. Valtix Gateways in the security VPC run an auto scaled set of instances that can automatically scale in/out based on traffic load. Existing or new VPCs can be protected for ingress, egress, east-west and PaaS traffic.
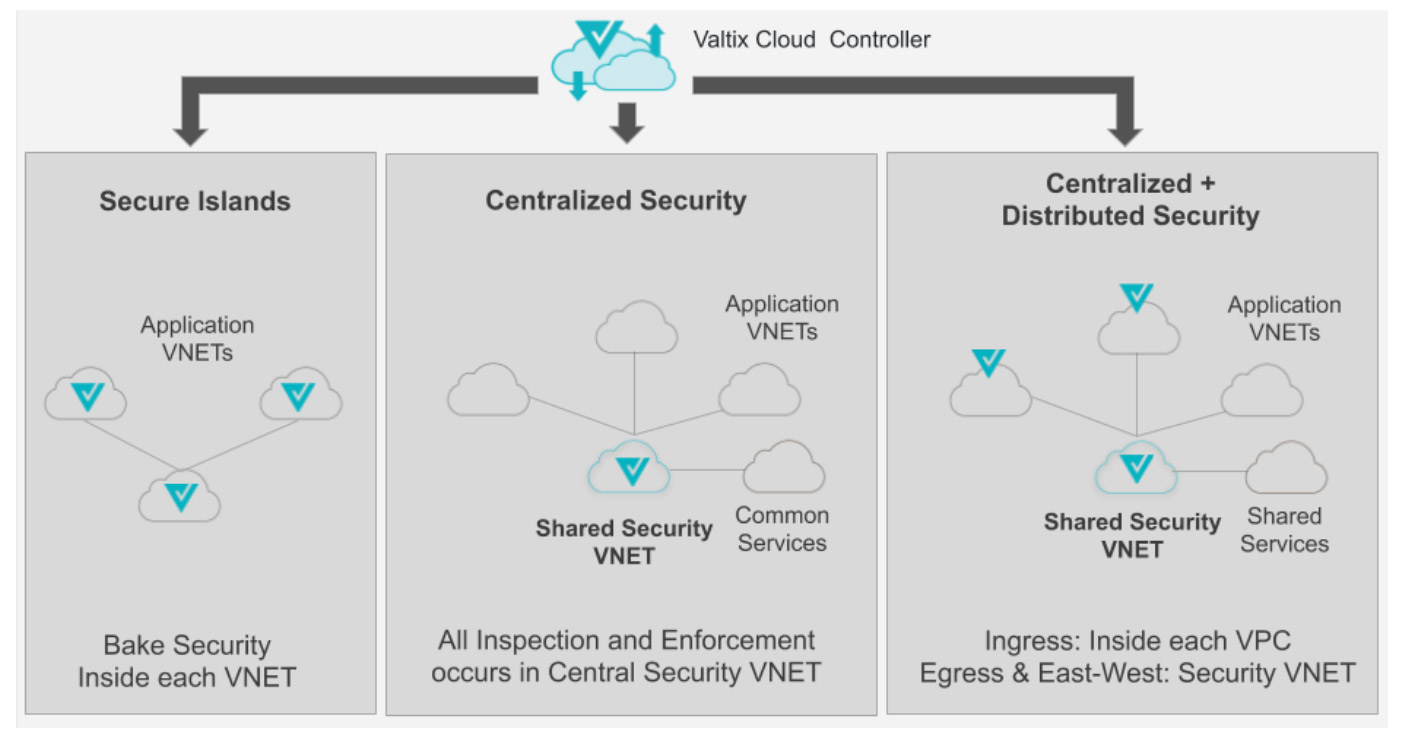
Improvements in Azure Deployments
Valtix Gateways can be deployed inside each VNET to create secure islands, and/or deployed as a centralized security stack across multiple VNETs as a hub-n-spoke design. This release allows you to simply deploy a Valtix Gateway for either architecture without explicitly selecting Edge mode or Hub mode.
DataDog Integration
Traffic and threat logs can now be sent to your DataDog environment, in addition to the existing support for Syslog and Splunk. This gives you more options for log storage, and security incident and event management (SIEM). DataDog can be used for collating data across multiple sources for analytics, visualization and insights. This enables incident response (IR) and security operations center (SOC) teams to use the deep packet inspection logs
