Version 2.1 of Valtix Cloud Security Service brings a massive transformation in helping customers secure their applications running in public clouds. This delivers on the core promise of Valtix: discover your applications/workloads, deploy Valtix security services and defend your discovered applications – all in less than 1 hour. This post highlights a few of the most requested features from customers. This release comes six weeks after version 2.0, highlighting the speed of innovation and power of SaaS platforms to continuously deliver value. Customers can, with one-click, deploy these updates in a cloud-native blue-green style update with no downtime.
- Egress and PaaS Security (Forward Proxy with TLS decryption) – allows Valtix to be scaled out as a forward proxy with TLS decryption on both AWS and Azure to inspect outbound traffic from the VPC/VNET. This works in both Edge mode (Valtix deployed inside a VPC/VNET) and Hub mode (Valtix deployed as a security service in transit designs).
- URL Filtering for Egress and PaaS traffic – Apply controls to enable a safelist or block list of sites permitted. For example, this gives granular control to github.com/myOrgrepo versus basic FQDN controls like github.com.
- Application Identity – Use deep packet inspection (DPI) to identify thousands of applications and allow/deny access based on policy.
- Software Dependency Management – Provides one-click upgrades to the Valtix Cloud Firewall fleet.
- AWS IPSec for VGW and TGW – Enables Valtix Controller to orchestrate IPSec VPN from your VPC’s VGW or Transit Gateway (TGW) to an IPSec endpoint such as an on-premises VPN appliance or firewall. This adds to the existing support for orchestrating IPSec connections for Azure VPN Gateway.
- Usage and Metering dashboard – Track daily usage of Valtix services.
- TCP/TLS Proxy – Enables security of Internet-facing non-web applications such as RDP.
- Bug fixes and enhancements – As a SaaS platform Valtix continually fixes bugs and provides enhancements behind the scenes without any customer outages.
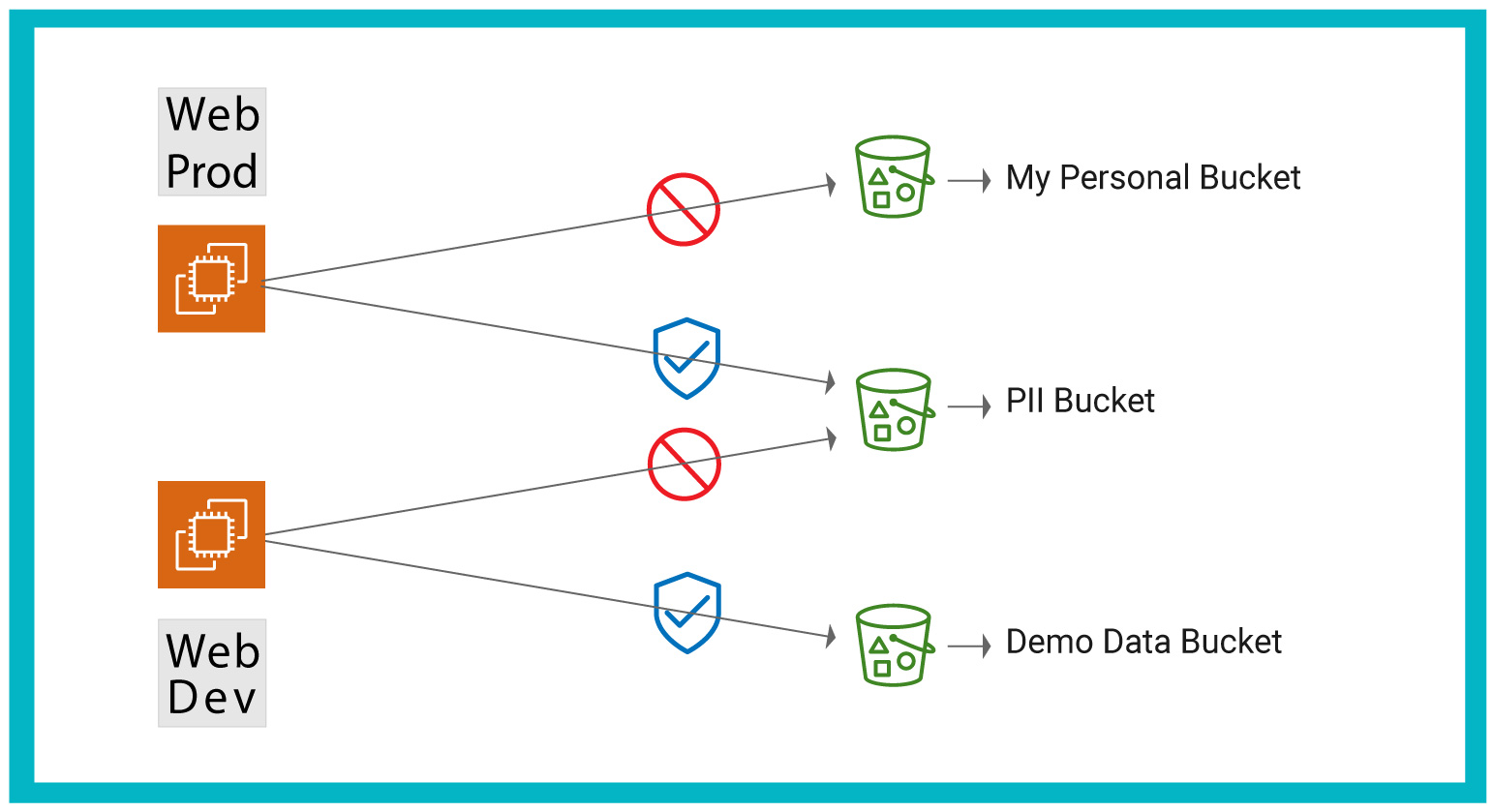
Prevent Exfiltration from Cloud Storage Buckets
A key problem in securing public cloud infrastructure (both IaaS and PaaS) is that the native cloud controls (security groups and access control lists) do not inspect the traffic to prevent data exfiltration and connections to bad sites like command-and-control sites or known malicious locations. By default the security groups are open for all outbound traffic and there is no simple way to (a) allow safelists of sites (b) allow access to approved/known PaaS like the company’s approved AWS S3 buckets, but block use of personal S3 buckets, (c) allow only approved application traffic based on machine identity.
For example, if an instance has access to an Azure storage blob with confidential data, how does one stop a malicious user (internal or attacker) from copying this data to a personal location?
Valtix now allows customers to do deep inspection of outbound/egress and PaaS traffic using a layered set of policies:
- Forward proxy with TLS decryption
- Source and destination defined as workload tags (web, dev, test, pci, VPC, security groups…), IP addresses, FQDN or URLs (later two are for destinations only)
- Application identification – allow wget, allow apt-get, block MYSQL
- URL Filtering – Allow or deny based on safelist or block list of sites including PaaS like AWS S3 buckets or Azure blobs
- IDS/IPS – inspect the flows to ensure malware is not being sent/received
Here’s an example of what’s possible with Valtix:
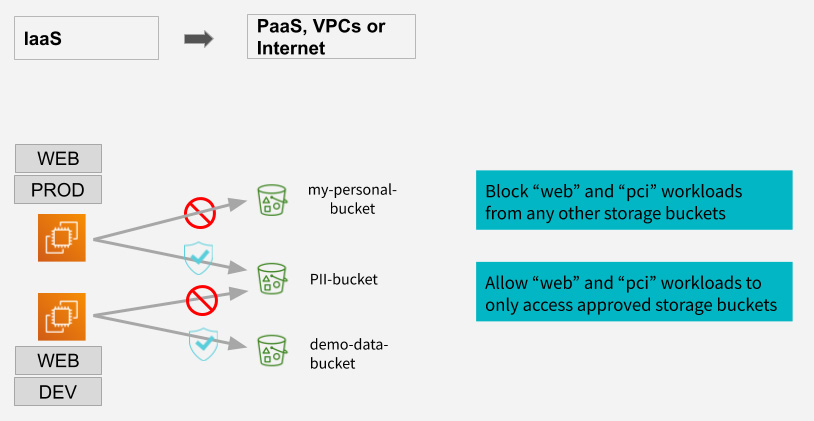
- Allow “web” and “pci” instances to access the org’s approved AWS S3 buckets or Azure storage blobs.
- But block a malicious insider or bad actor on the “pci” instance from connecting to a personal S3 bucket to exfiltrate data. This can happen even if the bad actor has credentials for their personal bucket.
- These features ensure that data cannot be stolen from a corporate/organization storage bucket and copied to a personal bucket.
And of course, flow logs enhancements show details about the egress URLs being accessed. This data is available in a fast, responsive, ElasticSearch within your Valtix Controller portal for upto 30 days. Additional analysis and alerting can happen with log forwarding to your syslog-based SIEM or Splunk environments.
URL Filtering and Application Identity
A well known strategy for preventing attacks and stopping malicious actors is to safelist the URL destinations and applications that should be allowed. This prevents them from exploiting vulnerabilities in the applications and connecting to command-and-control sites or malicious destinations. Valtix now makes it easy to define this as a global set of security rules that can be centrally deployed across multiple clouds, VPCs/VNETs and applications, or customize them on a case-by-case basis.
More importantly, a URL-based control (github.com/myOrgRepo) is significantly more secure than a basic FQDN control which in the case of GitHub can include several malicious repositories. This ensures that production or compliance-oriented workloads are protected from malware and backdoors.
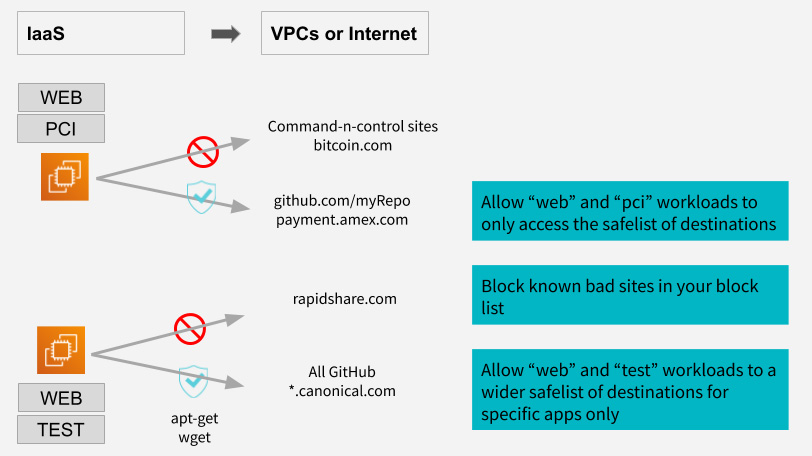
The example below shows how Valtix Gateways (auto scaling fleet of VCFs), deployed inline to the traffic, will:
- Allow a payment gateway’s production instances tagged “web” and “pci” to access safelist sites such as amex.com, and also to the company’s GitHub repository which may contain their infrastructure-as-code (IaC) components.
- But those same instances cannot connect to malicious sites.
- Similarly, “test” systems can connect to *.canonical.com to perform software updates (say apt-get for Ubuntu Linux systems) only. The test systems also may have wider access to the entire GitHub site rather than just the company’s repository. This may be because the dev and test systems may need wider access, while production systems might be restricted to a narrower safelist.
Usage and Metering Dashboard
Public clouds are all about elasticity and on-demand deployment. Valtix supports a cloud-native auto scaling engine, customers simply define the minimum and maximum number of Valtix Cloud Firewalls to deploy in each Valtix Gateway, across 2 or more availability zones. The Valtix Controller automatically does all the scale out and scale in magic. There are no complex templates to deploy, no AWS Lambda or Azure Functions to manage, no pub/sub queues or licensing activation/deactivation details to worry about.
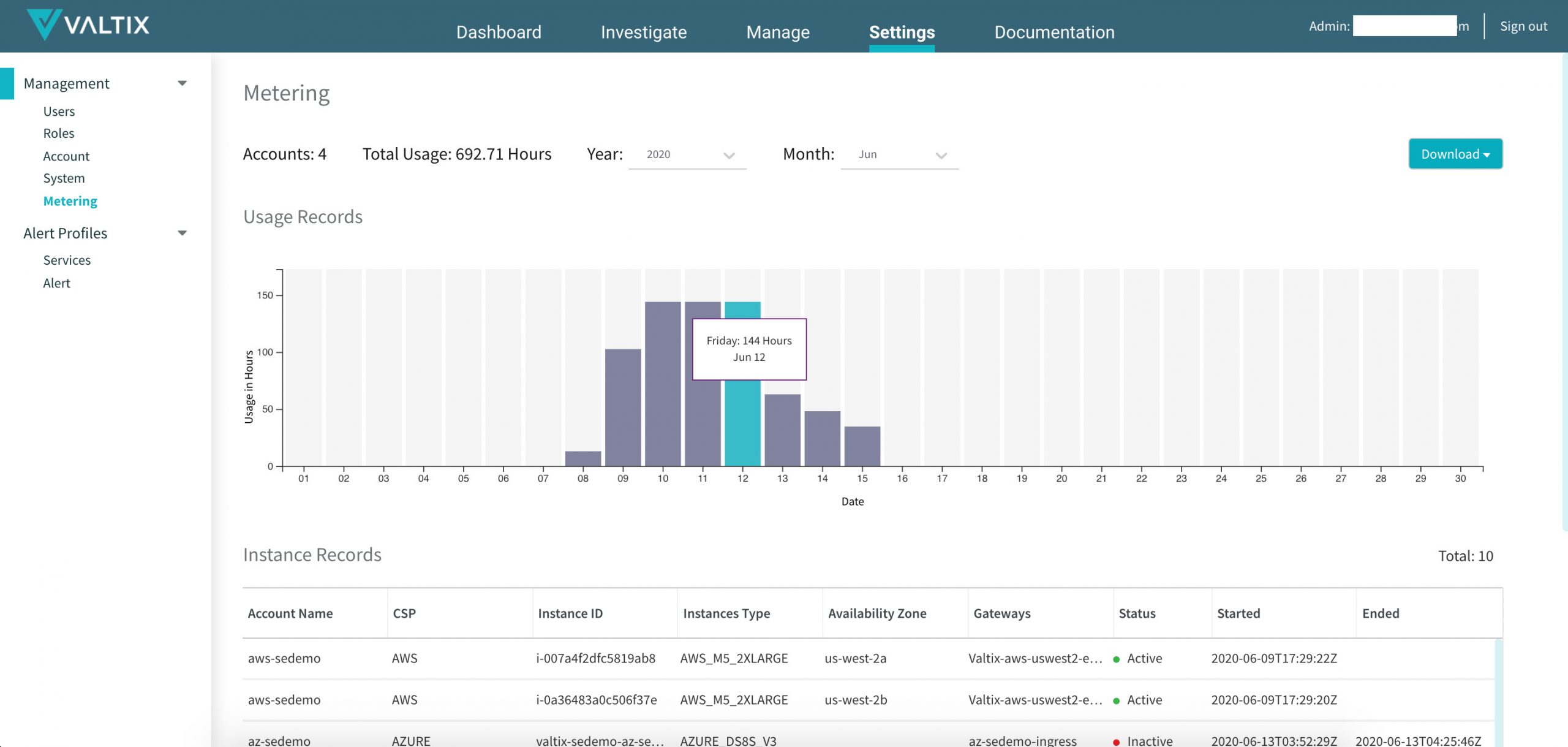
This simplicity is now easily accessible. Go to Valtix SaaS portal > Settings > Metering to see:
- Daily usage by month: number of hours Valtix Cloud Firewall (VCF) are running each day of a selected month
- List of VCF instances with details: start and stop times, instance id, cloud region/zone, associated Valtix Gateway
- Download a CSV file for usage and VCF instance information for the entire month
Metering records allows customers to reconcile their monthly invoices and manage their cloud security costs. This provides true, cloud-style, pay-as-you-go (PAYG) metering records across each of your Valtix Gateway deployments. Compared to traditional firewall appliances which are often running under-capacity and hence wasting substantial money, Valtix provides a highly responsive auto scaling engine, with 3 second telemetry, to automatically manage the firewall fleet.