Valtix announces the availability of the Cloud Risk Assessment Report, which spots and highlights network security weaknesses and vulnerabilities – the readout will be available immediately after your 30 day test drive of the Valtix Cloud Security Platform.
Keeping up with Your Cloud Growth and Cloud Security Posture Management
As organizations take advantage of the cloud-native architectures to enable business efficiencies and accelerate service growth in Public Cloud, those organizations must also be aware of the fundamentally new challenges to securing those critical applications and workloads that have been migrated or deployed to cloud environments.
The benefits of using the on-demand and almost limitless compute provided by cloud service providers (CSP) enable elasticity and continuous deployments of business services and applications. The continuous and on-demand deployment of adds, moves and changes commonly seen within cloud environments is much different from the traditional on-prem data centers, where changes are planned ahead of time giving security and network teams advanced notice to react and apply the required security controls.
To secure and move in-pace with agile, cloud architectures, a new approach to securing cloud environments is needed. The Valtix Security Platform consists of 2 components: Valtix Cloud Controller and Valtix Cloud Firewall. The Valtix Cloud Controller uses a cloud-native microservices architecture that is highly-scalable to take advantage of available compute, and automated methods to continuously discover your cloud apps in this dynamic environment and deploy security as-needed to defend those apps, dynamically. On the other hand, the Valtix Cloud Firewall uses a single-pass flexible service pipelined architecture to provide enterprise-class data center network security for your cloud apps. These processes summarize the Valtix security workflow into three design fundamentals: Discover, Deploy and Defend.
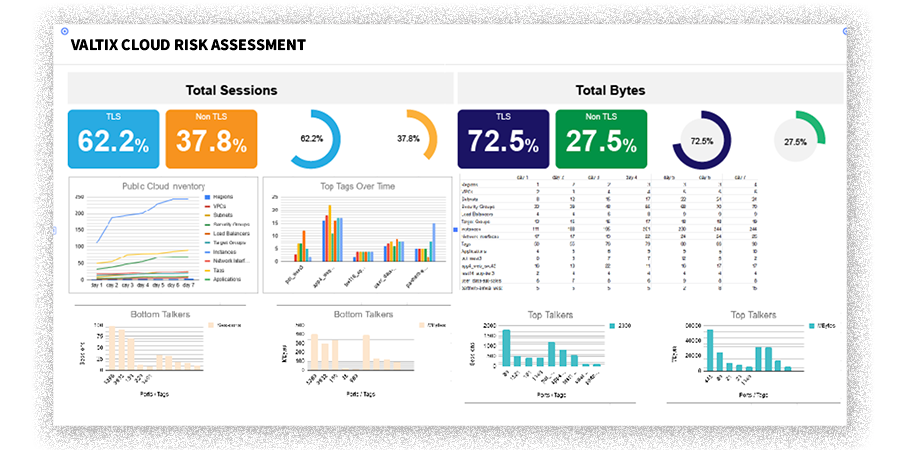
The benefit of this report is to provide the crucial information you need for security configuration and posture management.
Areas of cloud activity will be analyzed, and potential security risks will be highlighted to provide visibility into your cloud environments and where and how security controls can be placed within the cloud VPCs to reduce the risks and enable agility.
Key metrics highlighted in this report are:
- Encryption: use of encrypted traffic in your cloud environments
- Cloud agility: Measures the growth and dynamism in your cloud compute resources
- Cloud usage: Measures bandwidth usage in your cloud
- Top active apps and workloads in your cloud environment
- Identification of VPC to VPC communications
- Recommended security perimeters based on inter and intra traffic communications