Getting Started with Valtix using AWS Gateway Load Balancer (GWLB)
Outline
This guide will show you how to secure your cloud workloads against exfiltration on outbound flows to the Internet, and prevent lateral movement of attacks between VPCs (east-west). It is meant to be a technical how-to guide to walk you through an implementation for deploying AWS Gateway Load Balancer with Valtix Cloud Security Service.
Decision-makers can use this guide to understand how a security-as-a-service can protect their cloud assets by integrating security into their DevOps process.
The introduction of AWS Gateway Load Balancer (GWLB) will be seamless for our customers. Since Valtix is a multi-cloud security platform service, the infrastructure including the deployment of GWLB is managed by Valtix and therefore abstracted from the user.
How Valtix integrates with AWS Gateway Load Balancer.
Simplicity:
A key goal of moving to public clouds is to simplify the infrastructure by using services as building blocks, and focus on what is required to build, deliver and operate an application. Valtix is born-in-the-cloud and leverages cloud-native components to give an end-to-end security solution. Customers follow Discover (your cloud assets in real-time), Deploy (from Valtix SaaS portal or via Terraform Resource provider), and Defend (using security policies built with cloud discovered assets).
Scalability:
Prior to AWS Gateway Load Balancer, Valtix used the AWS Network Load Balancing (NLB) to support resilience and auto-scaling of the Valtix Gateway for egress and east-west. Using the NLB for egress and east-west meant that the AWS NLB service quota of 50 listeners per load balancer, Valtix would support up to 50 ports per Gateway. This quota is likely more than what most customers would need for Internet-facing apps, but can be a limitation for egress and east-west (between VPCs).
AWS Gateway Load Balancer will remove that limitation and allow all TCP or UDP ports to be exposed to the Valtix Gateway through the use of Generic Network Virtualization Encapsulation (GENEVE). We’ll leave the coverage of this topic to our friends at AWS. This results in simplifying the security group configuration to only require UDP port 6081. Gateway Load Balancer also eliminates the provisioning time of a policy rule from minutes to seconds as there is no need to wait for network load balancer target health check for each rule that uses a new port.
Reduce Infrastructure Costs:
Existing customers needed to deploy separate Valtix gateways to support east-west (VPC to VPC) traffic flows as well as egress (internet outbound) traffic flows. With Gateway Load Balancer, these functions would be consolidated into a single Valtix gateway. Additionally, Valtix had previously deployed additional EC2 instances to support transparent forward proxy for egress. These instances were completely managed by Valtix as part of an egress gateway. Although Valtix did not charge additional costs to run these instances, customers did have to pay for the running costs of the EC2 instances that are no longer required.
Deploying Valtix with AWS Gateway Load Balancer
Below is an outline on how to deploy Vatix with AWS GWLB:
- Discover – on-board your AWS accounts using Valtix Controller SaaS portal or Terraform template using Valtix Terraform resource provider. This creates a real-time inventory of the cloud infrastructure (VPC, EC2 instances, load balancers, subnets etc) in the customer’s AWS accounts.
- Deploy – the Valtix Gateways with auto scaling settings (set min/max per availability zone). This includes an option to use AWS Gateway Load Balancer in supported AWS regions.
- Defend – Create security policies, with a layered set of inspection policies, using the cloud assets discovered.
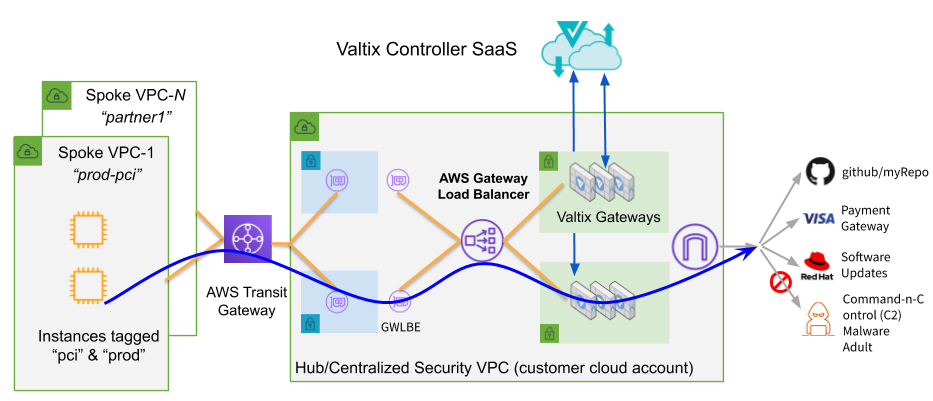
The steps below will walk you through steps to creating a hub-and-spoke design for securing multiple spoke (application) VPC’s connected to a Valtix Security VPC (the hub, also known as a Services VPC) using AWS Transit Gateway.
1. Discover: Onboard your AWS Accounts
- Login to your Valtix Controller SaaS portal. Refer to Valtix Controller > Documentation > Setup Guides > AWS Setup Guide. This will walk you through the steps to grant the relevant IAM permissions for Valtix to discover your cloud assets. You can also use Terraform to onboard one/more AWS accounts.
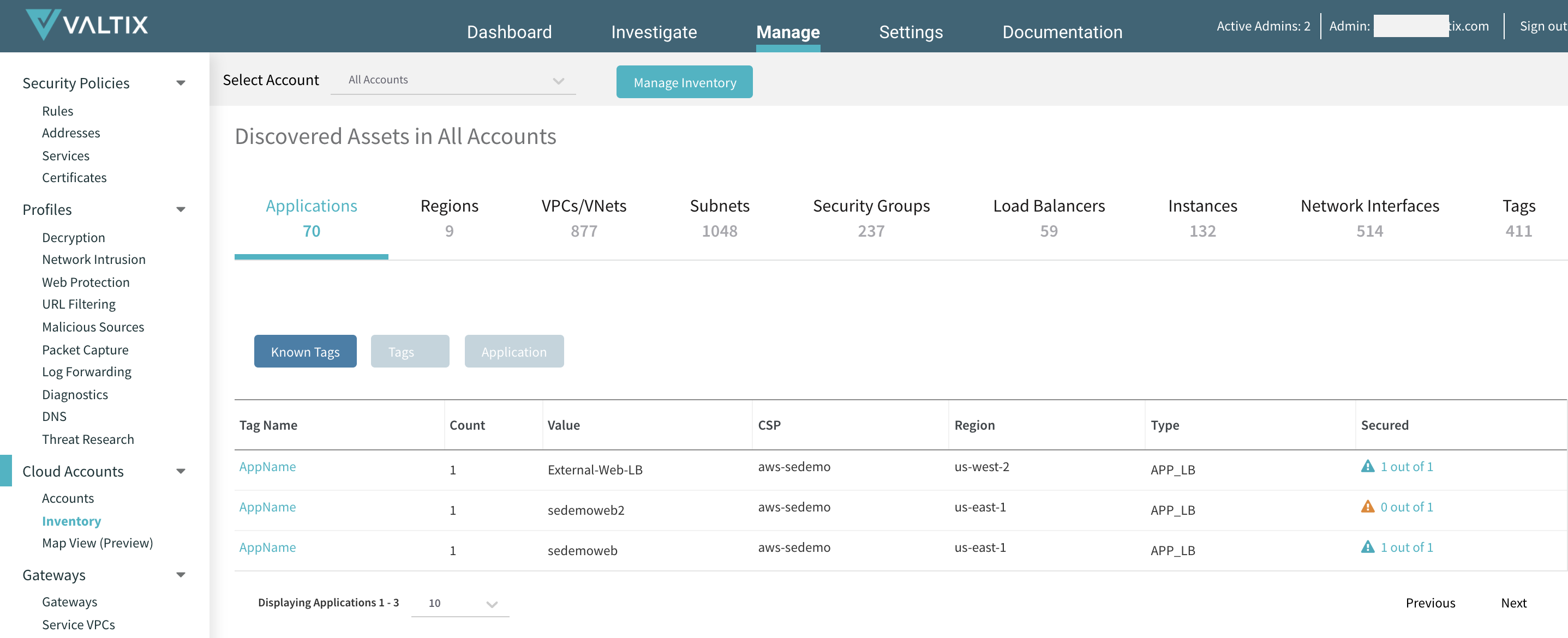
- Review the inventory of your cloud accounts from Valtix Controller > Manage > Cloud Accounts > Inventory. This is continually refreshed in near real-time as instances are added/removed. You can also select specific tags of your cloud assets to be visible in the “Known Tags” inventory by configuring them in Settings > Account > Application Tags. For example, tag name “Prod” or “PCI” can highlight them to make them visible more clearly. This allows security teams to focus on which apps to focus on first.
2. Deploy Valtix Gateway in a Hub with AWS Gateway Load Balancer
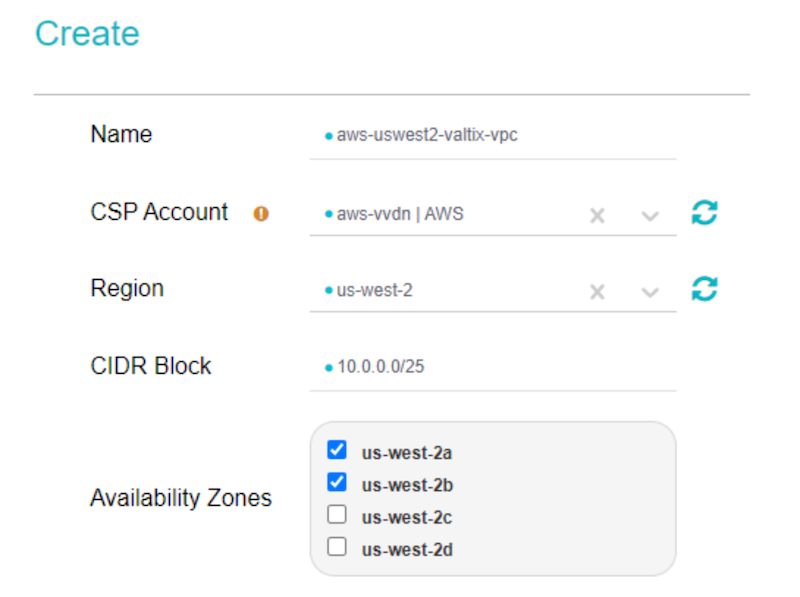
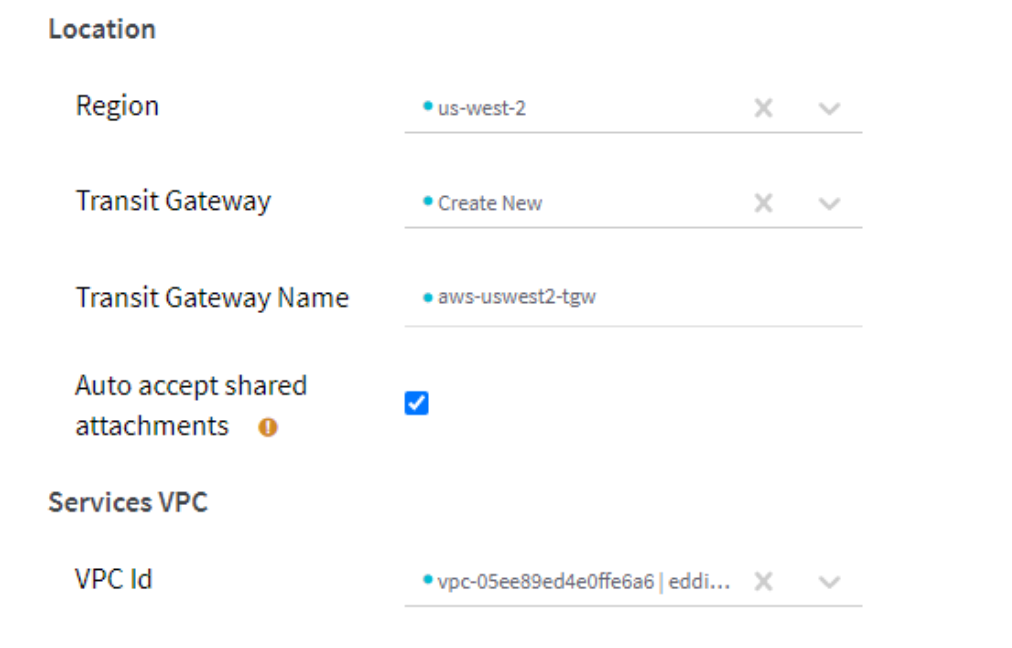
- In Valtix Controller > Manage > Gateways > Services VPC: click on Create VPC button. This creates the hub VPC that where security inspection will take place for the east-west and egress traffic. This services VPC will be attached to an AWS Transit VPC to which your spoke VPCs with applications are connected.
Note: At launch*, AWS Gateway Load Balancer (GWLB) is supported in 5 regions. Once AWS expands availability, Valtix will automatically enable those regions.
- From Manage > Gateway: click on Add Gateway. Select an instance type (m5.2xlarge is recommenced) and set min\max values for the auto scaling settings. Enable the AWS Gateway Load Balancer checkbox.
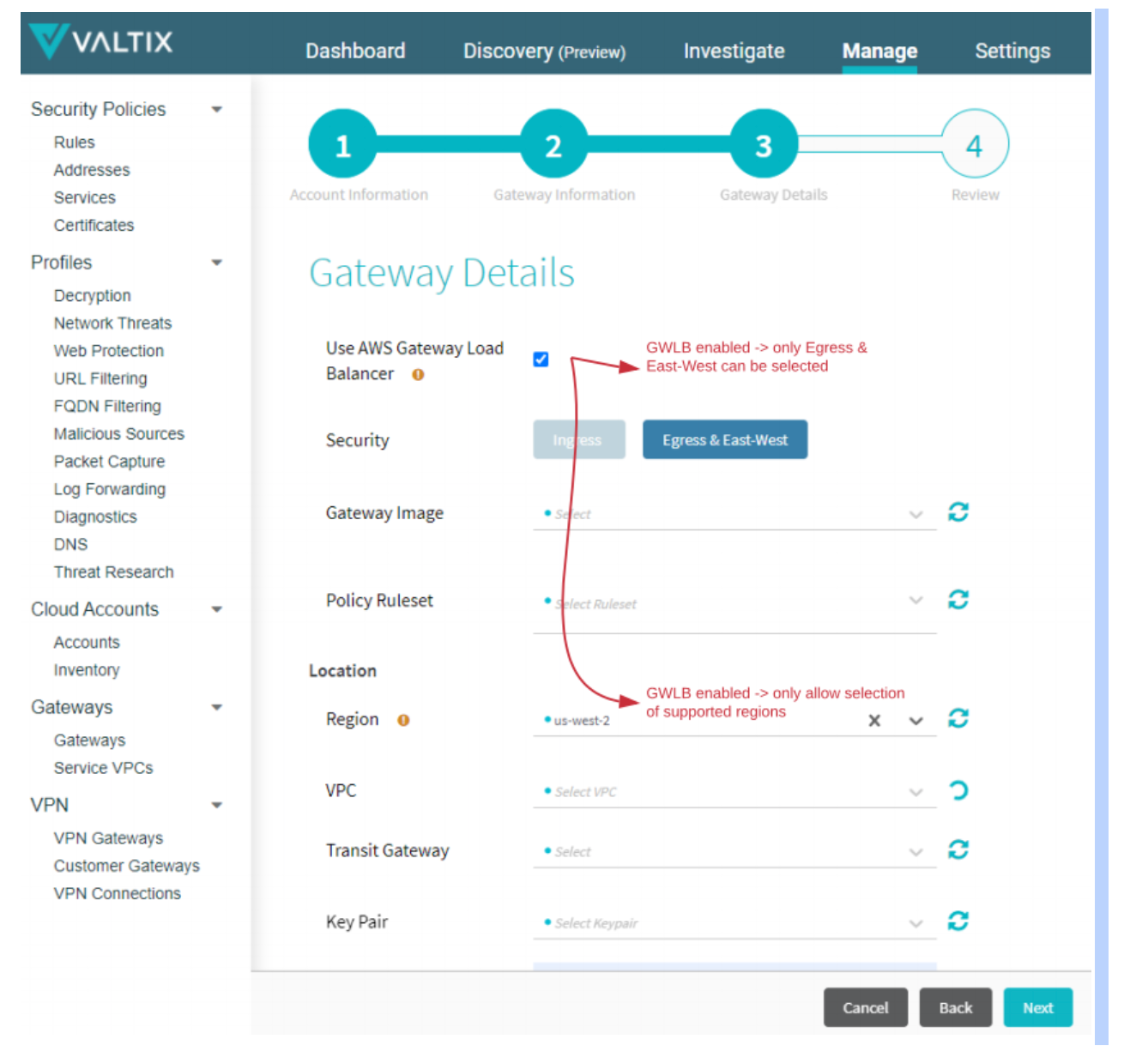
Review the Gateway Configuration and select Finish to create Valtix Gateway
The only difference in the create egress workflow is the selection of the GWLB option checkbox and validation that the Valtix Gateway is being deployed in a supported AWS region. This exemplifies how as a network security service, Valtix can leverage AWS innovations seamlessly into our cloud-native architecture to deliver benefits without the complex scripting often seen with DIY virtual firewall appliances.
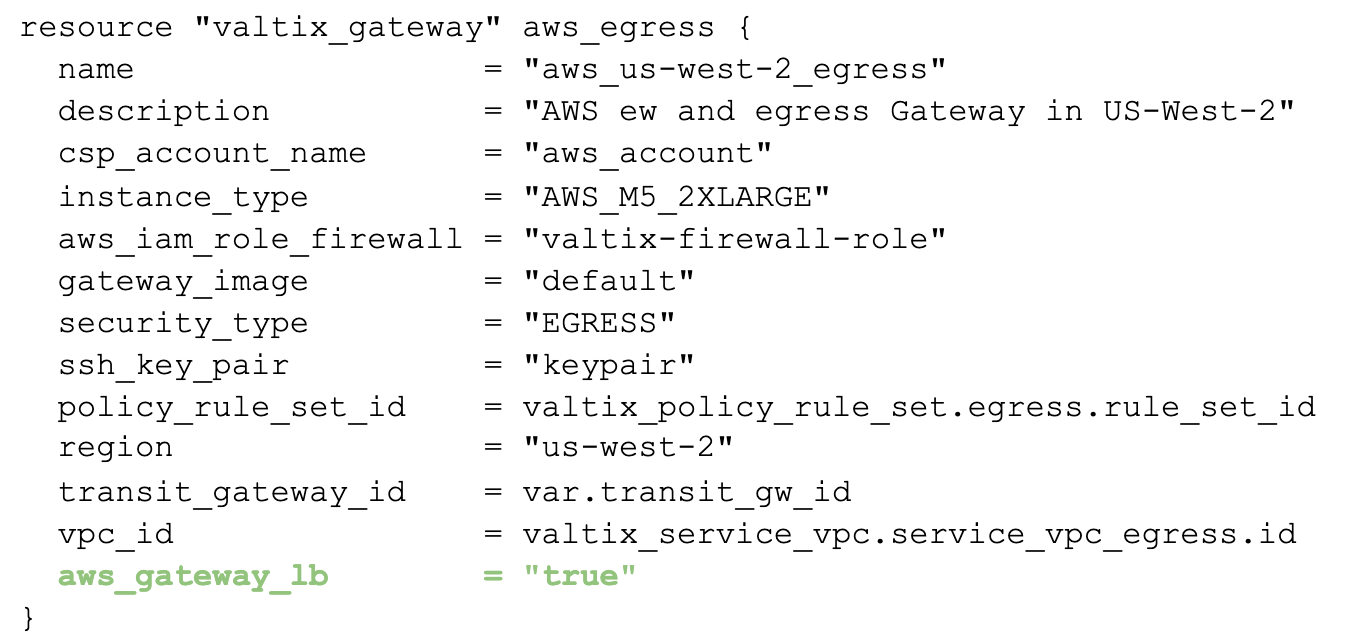
Terraform Resource Provider update
Much like the interactive UI deployment, the Valtix Terraform Resource Provider has been updated to support Gateway Load Balancer. Similar to the UI workflow, there is only one additional attribute of the resource definition that needs to be added to use Gateway Load Balancer:
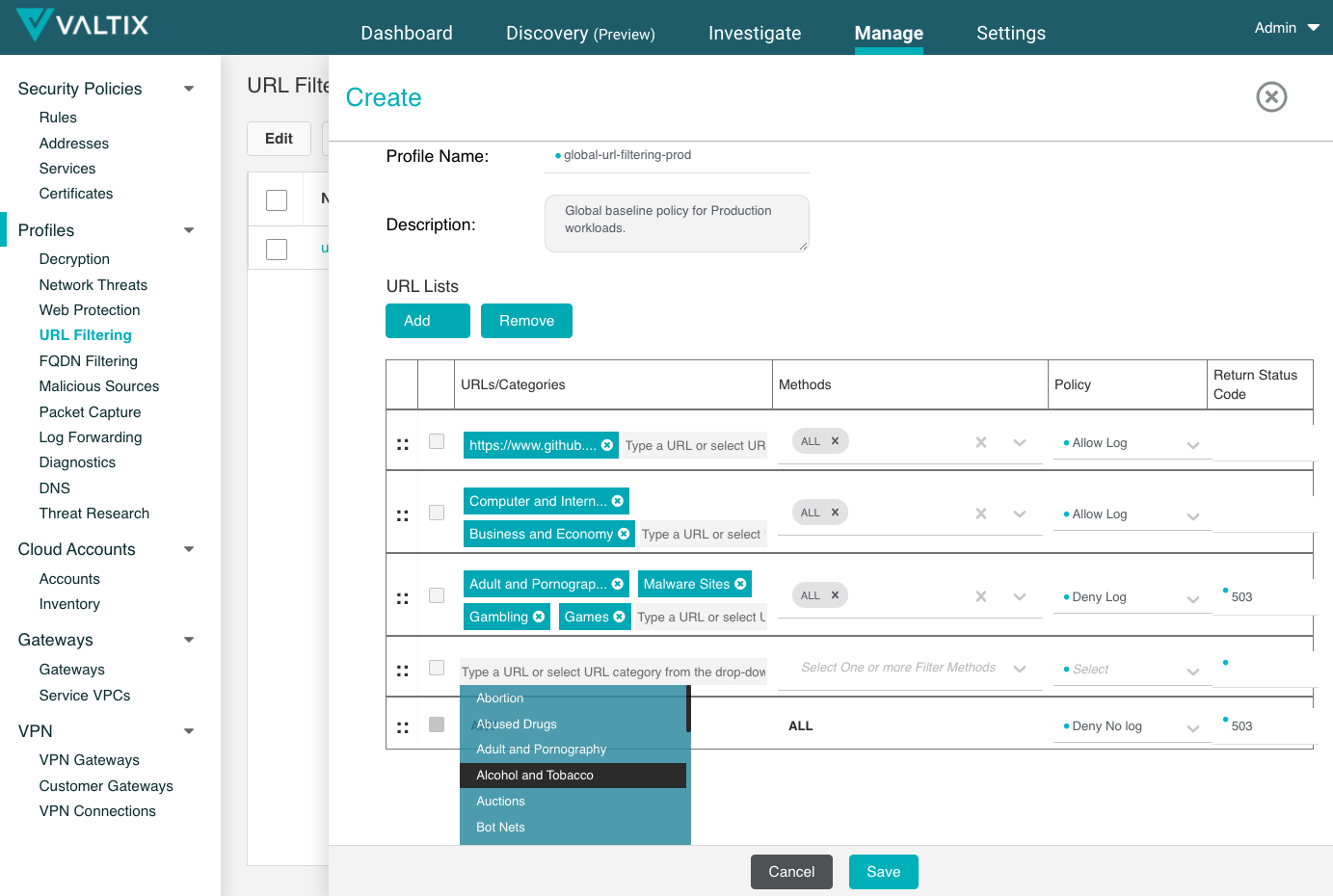
3. Defend
Now you can define security policies using discovered cloud asset tags. For example: allow “prod” systems to access only the org GitHub repo (github.com/myOrgRepo), “dev” can access all of github.com, “pci” apps can access “Financial Services” sites and everyone is blocked from all “Malware” and “Adult” category URLs/sites. You can layer on relevant DLP policies for SSH keys, credit card numbers and 30 other patterns or any regular expression (REGEX) to protect your data in motion.
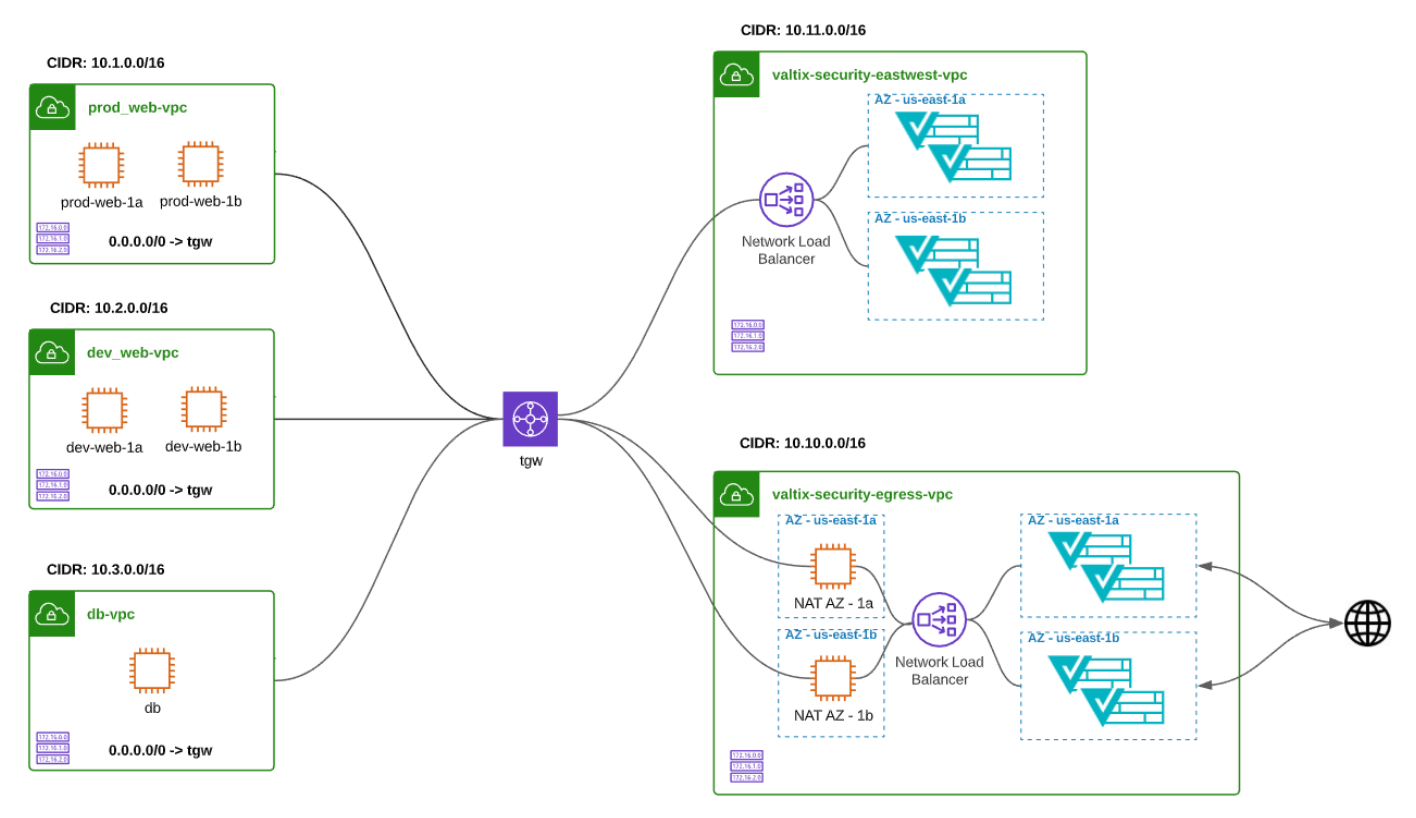
A World Without AWS Gateway Load Balancer
As mentioned earlier, one of the key advantages of Valtix with AWS Gateway Load Balancer is the ability to consolidate east-west (inter-VPC) and egress (outbound to Internet) and services VPCs into a single deployment. Below is a diagram of for these functions prior to AWS Gateway Load Balancer:
As you see in the egress security VPC, Valtix previously deployed a NAT instance to support transparent forward proxy and auto-scaling of the Valtix Gateways. With GWLB this function is no longer necessary therefore eliminating the need for additional EC2 in the gateway deployment. Valtix deploys and manages the life cycle of the gateways so for customers this was an implementation detail that was visible only in the AWS console.
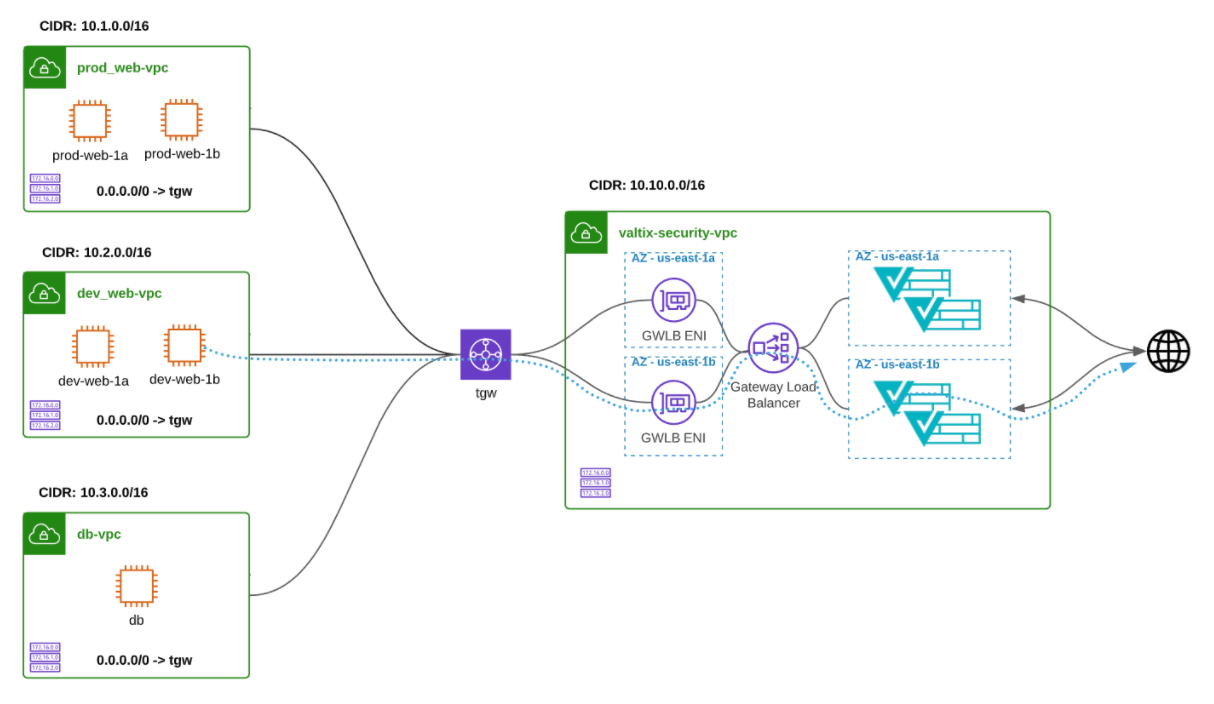
The below diagram shows the new reference architecture for centralized security model with AWS Transit Gateway and Gateway Load Balancer for inter-VPC inspection (east-west) and Internet outbound inspection (egress).
This also has the downstream effect of simplifying the Transit Gateway VPC attachment route tables that Valtix orchestrates as part of our simple “protect VPC” workflow. Prior to Gateway Load Balancer, Valtix would have to automate the Transit Gateway routes for “protected” spoke VPCs to route traffic to both the east-west service Transit Gateway VPC attachment (10.11.0.0/16 in this example) as well as a default route (0.0.0.0/0) to egress service Transit Gateway VPC attachment. With Gateway Load Balancer, Valtix will only need to orchestrate the default route to the single Transit Gateway VPC attachment for the egress services VPC. Small adjustment but anything we can do to simplify routing is welcome at scale.
Availability
Valtix Gateway Load Balancer support is available now in all AWS regions that support Gateway Load Balancer (GWLB). As of this blog’s post, this is currently available in the us-west-2 (Oregon), us-east-1 (N. Virginia), eu-west-1 (Ireland), ap-southeast-2 (Sydney), and sa-east-1 (São Paulo) regions. As Gateway Load Balancer becomes widely available across regions, Valtix plans to using AWS Gateway Load Balancer as the default scale out option.
References
- AWS Gateway Load Balancer announcement
- Valtix AWS security
- Video Demo (8 min) – Getting Started with Valtix using AWS Gateway Load Balancer
- Valtix Cloud Security Service in AWS Marketplace
- To learn more contact us at awssales@valtix.com