Summary
On 08-Dec-2020, FireEye revealed{: target=”blank”} that a state-sponsored adversary stole red team tools used by their internal security researchers to mimic a potential adversary’s attack or exploitation capabilities against an enterprise. This attack is related, in part, to the wider SUNBURST{: target=”blank”} attack on the Orion management software from SolarWinds.
It will take time for attackers to understand the capabilities of these red team tools and use them in attacks. Valtix has used the information provided by FireEye to ensure that customers can protect themselves. Deploying these rules will take only a few minutes (call it the power of a SaaS platform).
What Valtix is Doing to Keep Customers Secure
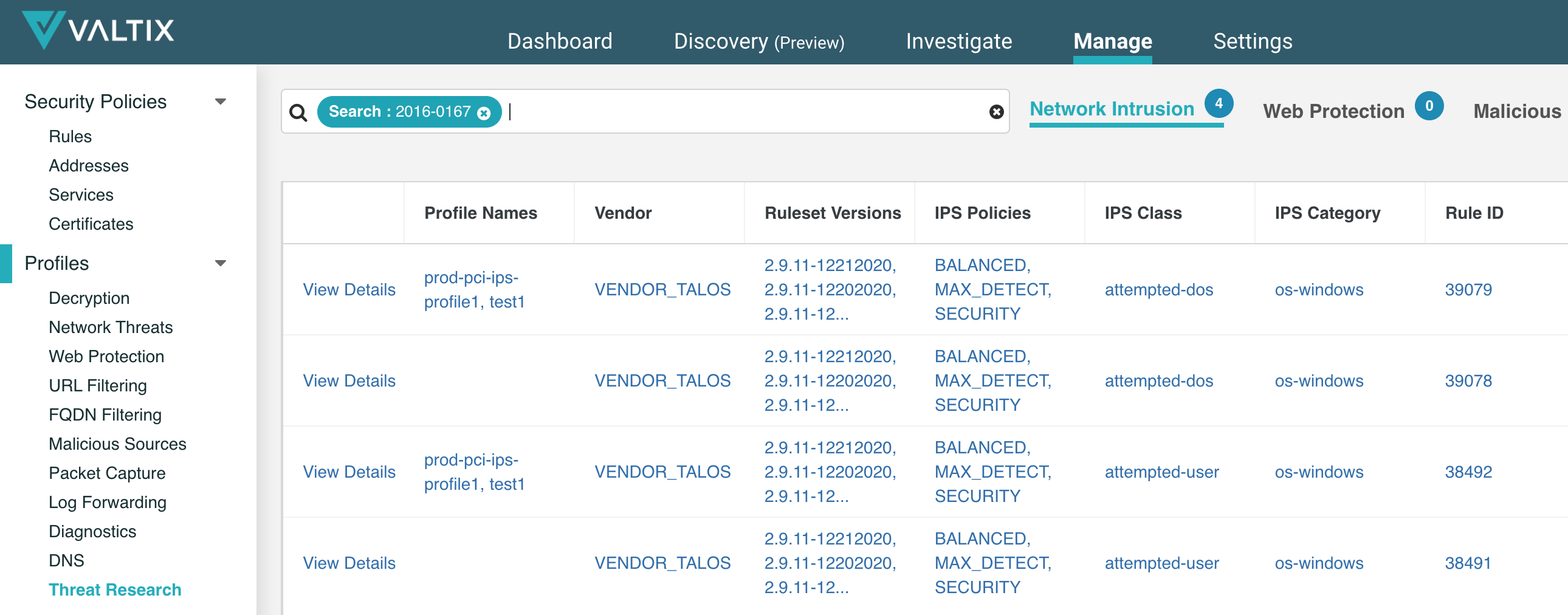
Valtix has verified that our existing automation continuously provides the latest signatures/rules for IDS/IPS and antivirus include the countermeasures published by FireEye{: target=”_blank”}. This allows customers to deploy the necessary protections to defend against the red team tools stolen from FireEye. You can search for the specific CVE’s in your Valtix Controller > Manage > Threat Research. For example, below shows a lookup for CVE-2016-0167 and which existing IPS profiles currently already include the relevant protections.
Steps to Protect Your Public Cloud Infrastructure
Customers should deploy these rules in their IDS/IPS and antivirus profiles as soon as reasonably possible. Deploying them literally takes two clicks, here are the steps:
- Login to your Valtix Controller portal.
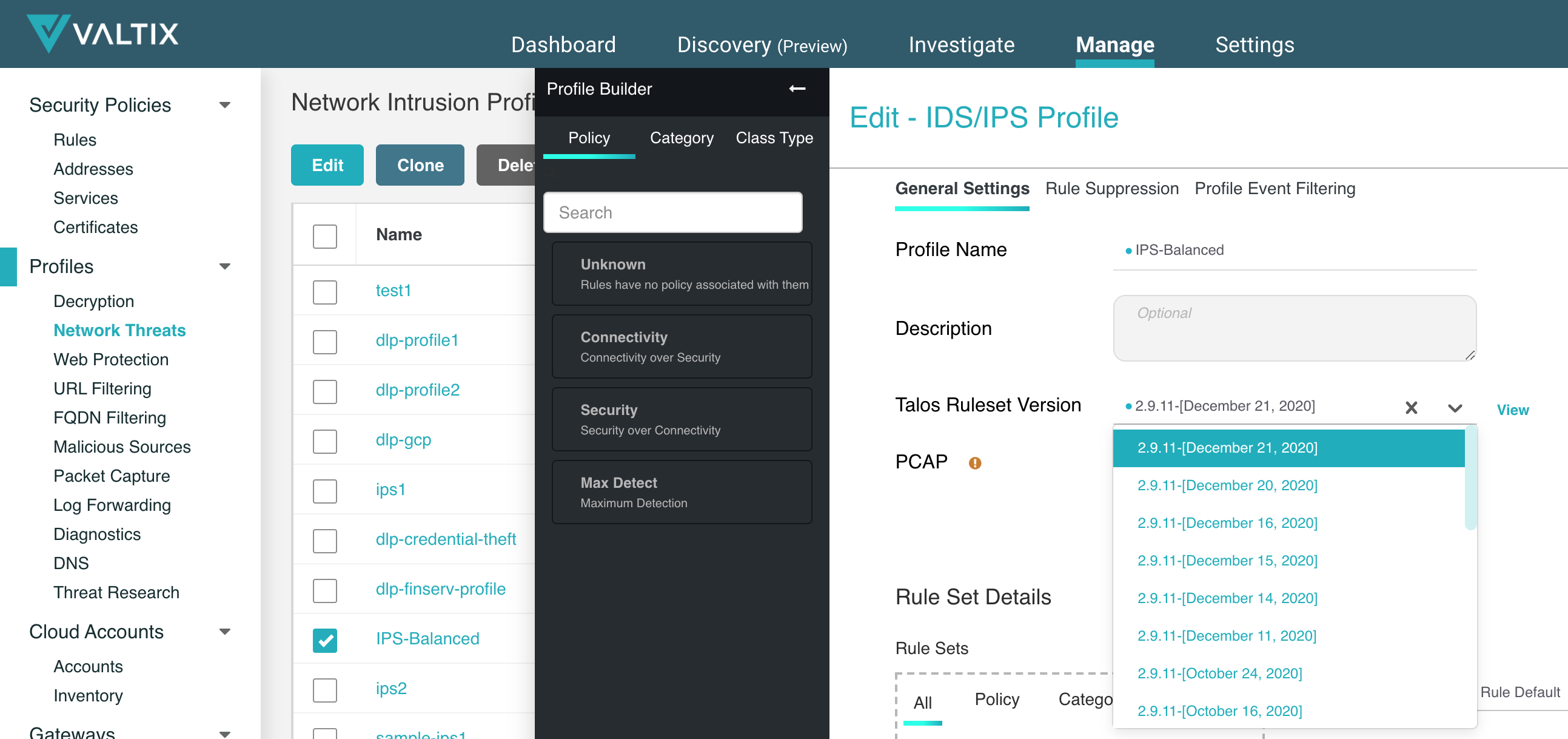
- Go to Manage > Network Threats, select the checkbox for the IDS/IPS profile in use, click Edit.
- For Talos Ruleset Version select the latest version available.
- Apply the same steps for any Antivirus profile that is in use.
Note:
- If you maintain a test/staging environment for testing security policies and rules, ensure that you test these updates against them first before rolling them out to your production systems.
- You can also check/confirm the relevant CVE’s by clicking on the “View” link next to a ruleset version or check the Threat Research tool mentioned above.
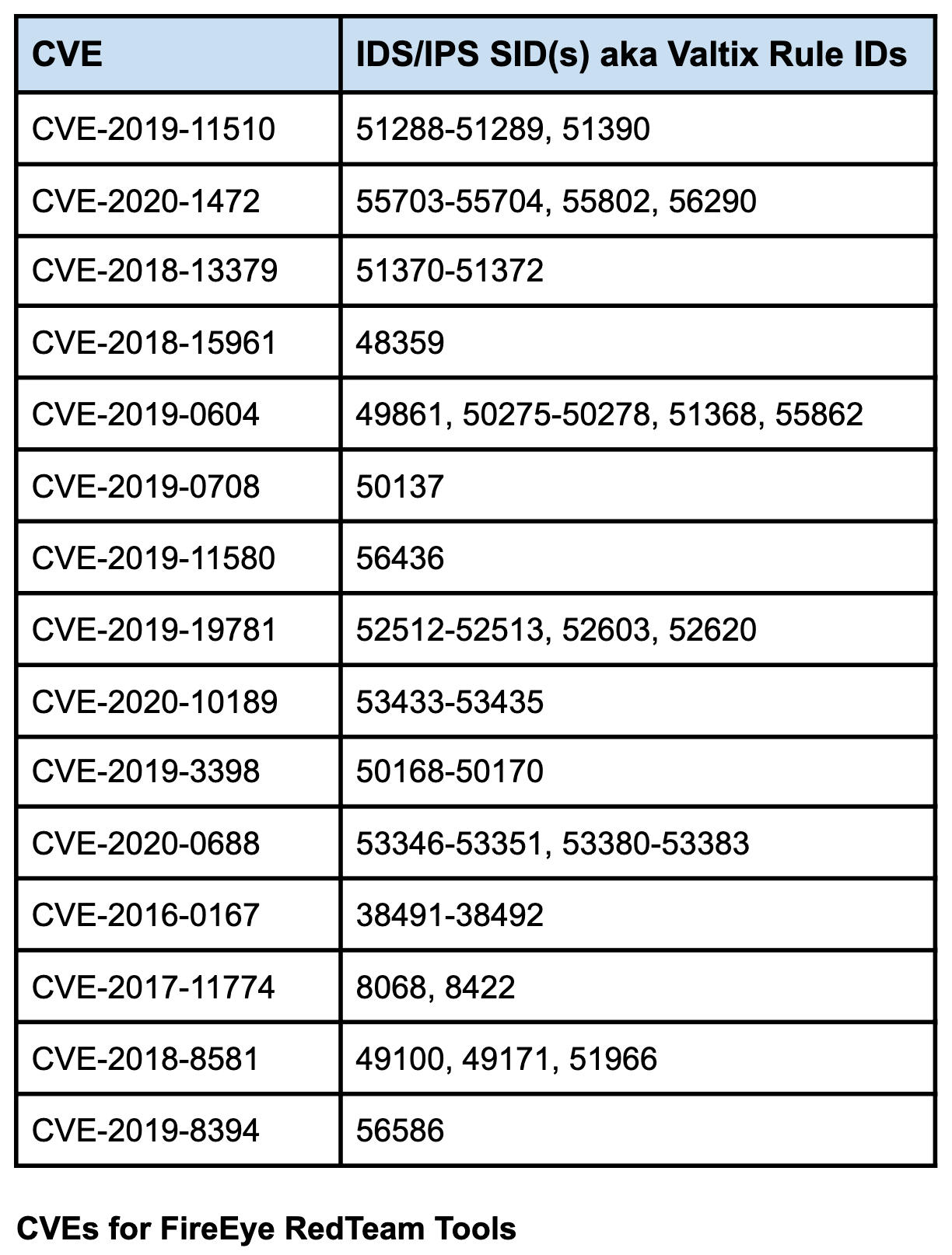
- Valtix has provided coverage for the CVEs related to the FireEye incident at the bottom of this post.
Security is Job #1 for Everyone
Valtix provides network security for protecting public cloud workloads of customers across financial services, healthcare, manufacturing, retail and other industries. We take this responsibility very seriously and have two major initiatives:
- Automate everything we can, so you can focus on what can’t be automated For customers: This means that as a security-as-a-service (SaaS) customers can discover, deploy and defend their cloud infrastructure within minutes, not weeks or months. This gives security teams more time to focus on creating relevant security policies, analytics and incident response.
- For Valtix: This means that our internal systems use continuous integration and continuous development (CI/CD) to integrate all relevant tooling to make the life of our teams that perform quality assurance, software build, software release, and site reliability engineering (SRE).
- Securing our internal systems. To secure the internal systems of Valtix we follow the following, among others, processes:
- Securing coding practices
- Code reviews
- Scan for vulnerabilities
- Penetration testing
Valtix Coverage for FireEye Red Team Tools