Summary
HashiCorp’s Terraform has become a popular method for automating deployment of workloads on public clouds and on-premises environments. Security teams are also adopting Terraform to automate their workflows. Valtix previously released a Terraform plugin, also known as a provider, that allows customers to deploy their applications and security with a single configuration file.
Customers are using this to bake security into their DevOps workflows with no compromises, i.e. no additional supporting Go, Python scripts or Ansible modules are needed. This update announces that Valtix is now releasing an official aka HashiCorp verified Valtix provider for Terraform.
Also, documentation is now publicly available at docs.valtix.com. Previously this was embedded inside each customer’s SaaS portal login.
Cloud Speed A Go? Duct Tape & Wires Edition
Without Terraform, automating security requires using the security vendor’s SDK or REST API’s and often use additional Python, Ansible or other libraries. This creates a kludgy solution full of duct tape and wires. Legacy security vendors such as next-generation firewalls (NGFW), secure web gateway (SGW), web application firewalls (WAF) and others have tried to provide Terraform providers, but they’ve simply done a retrofit job that tries to solve the problem. It is an ugly mess:
- More customized code with additional libraries and modules: a solution that is difficult to operate day-to-day, debug, maintain and support
- More dependencies
- Less flexibility
For example, a customer we worked with tried out a legacy NGFW vendor’s implementation and had to spend 2 months to get their entire implementation ready, and during runtime would take 20+ minutes for each deployment’s scaling decision: make a small change in auto scaling rules and 20 minutes later a new instance would be created.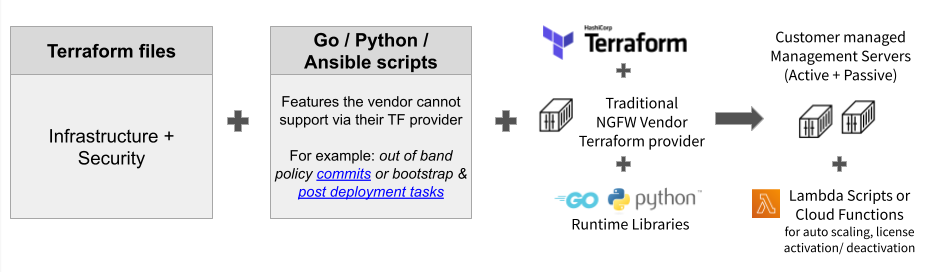
DevOps + Network Security: How to Terraform
Baking network security into the DevOps process should be simple, both for cloud operations and network security teams, and without lots of moving parts. Using Valtix, infrastructure as code (IaC) now truly becomes a reality. Valtix believes in the philosophy: Automate all you can, so you can focus on what can’t be easily automated, i.e. free up your people to do smarter things than mundane housekeeping tasks.
Valtix Terraform provider is part of the official release process of Valtix software, i.e. the provider covers all the features of Valtix and the provider versions are aligned with the Valtix Gateway software.
The Terraform files specify:
- Your application infrastructure details
- Cloud-specific services including load balancers, scale out details
- Compute workloads
- Cloud networking
- Valtix security policies
- Cloud account details, deployment region, VPC etc
- Auto scaling settings for Valtix Gateway instances: minimum = 1, maximum = 5 or 10 (based on max required) per availability zone (AZ)
- Globally consistent multi-cloud (AWS, Azure, GCP) security policies based on continuously discovered tags of the cloud workloads (across 10, 50, 100 or more VPCs and accounts on AWS, Azure, GCP)
- Egress\: [Forward Proxy] TLS decryption, IDS/IPS, antivirus, FQDN and URL filtering, DLP (based on data patterns: secrets, patterns for healthcare, finance, PCI, PII etc)
- Ingress\: [Reverse Proxy] TLS decryption, IDS/IPS, antivirus, DLP
- East-West (between VPCs): [Forward Proxy, Reverse Proxy, Forwarding] TLS decryption, IDS/IPS, antivirus, DLP, Application ID.
- To PaaS (cloud services accessed by FQDN or URL like AWS S3, Azure blobs, Amazon RDS…): [Forward Proxy] TLS decryption, IDS/IPS, antivirus, DLP, URL Filtering.
{: width=”659″ height=”188″}This operational simplicity brings the following benefits:
- 3 minute auto scaling events for new Valtix Gateway instances, make a small tweak in the TF files and grow/shrink elastically in response to demand… not the 30 minutes with legacy NGFWs
- Proper Terraform provider = plain and simple
- Completely automate all aspects of deploying Valtix Gateways and security policies since the Terraform provider covers all the features.
How to Get Started
- Valtix in AWS Marketplace & Azure Marketplace (GCP is also supported)
- Contact us for a free 30-day trial or learn more: [info@valtix.com](mailto:info@valtix.com?subject=Terraform and DevOps)
For more information see:
- Official Valtix provider for Terraform – docs and binaries
- Review Valtix Documentation
- Refer to Terraform examples in the Valtix GitHub repository
Terraform Example
Here are a few basic examples for using the Terraform provider. Refer to Valtix documentation for more details on generating the API key. Other examples can be found in the Valtix GitHub repository.
Initialize Provider
terraform {
required_providers {
valtix = {
source = “valtix-security/valtix”
} } }
provider “valtix” {
acctname = “valtix-provided-tenant-name”
server = “server-url”
port = “port-number”
api_key_file = file(var.valtix_api_key_file)
}
Add an AWS Account
resource “valtix_cloud_account” aws1 {
name = “awsaccount1”
csp_type = “AWS”
aws_credentials_type = “AWS_IAM_ROLE”
aws_iam_role = “arn:aws:iam::123456789012:role/valtixcontrollerrole”
aws_account_number = “123456789012”
aws_iam_role_external_id = “shared-external-id”
}
Add a Backend Address Object for Creating Policies
resource “valtix_address_object” app1-ag {
name = “app1”
description = “Backend App”
type = “STATIC”
value = [”10.10.10.10″]
backend_address = true
}

 {: width=”659″ height=”188″}This operational simplicity brings the following benefits:
{: width=”659″ height=”188″}This operational simplicity brings the following benefits: